

Skype is a wonderful piece of communications software for chat, voice and video. Unfortunately, after being purchased by Microsoft its security model was changed. In the good old days it used end-to-end encryption. That meant that nobody else except for the people communicating could understand the communication.s Microsoft changed that. Now, Microsoft can understand everything. And that means that any US government authority can force Microsoft to give them the communications. There seems to be alot of that.
Jitsi is a free and open source replacement for Skype which does preserve the end-to-end encryption. Thus, your communications are private. It uses some of the wonderful encryption technologies that were developed by cryptographers during the 90's and 00's which are available for general use.
Go to https://download.jitsi.org/jitsi/msi/ Choose MSI from the latest stable build (2.4 at time of writing). This takes you to a directory listing. Choose the file with 'latest'. E.g jitsi-2.4-latest-x64.msi

Run the installer. There is nothing complex about it.
When you start Jitsi you need to provide it with an account to use for chat. If you already have one fill it in.
It can also create one for you. Click on the 'Not registered yet?' at the bottom of the account dialog.
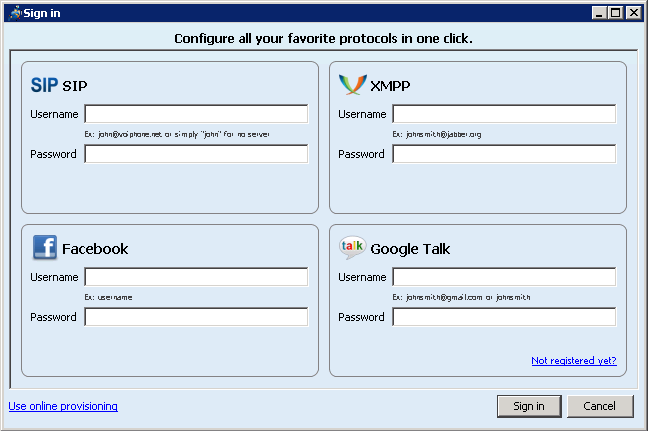
If you need to create and account I recommend XMPP. swissjabber.ch is easy and has good security.

Then you need to add contacts ...

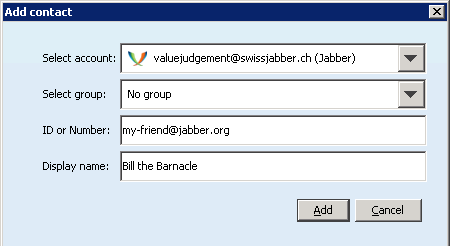
And they need to accept your contact request. You wait for them.

And they respond.
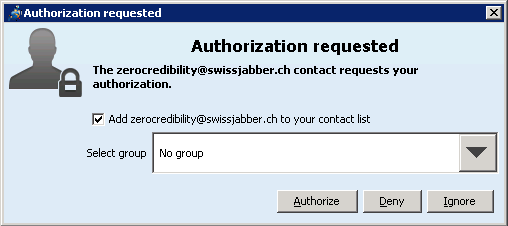
This is the most important bit. When you do this, you are done with setting up secure communication with whomever it is that you are trying to establish it.
You need to be sure that the person on the other end of the chat is really who they claim to be. Otherwise, its some nasty person pretending to be them and you are in a very bad place: thinking that your communications are encrypted (and they are) but being wrong about who you are talking to. Treat this bit seriously.
You need:
Because this is your first foray into encryption, it may also be your 'friends' first too. Thus, you dont have option 1 !! Thus, you need this piece of shared knowledge.
You type a question and an answer. They see the question and type an answer. If it matches (case sensitive), this counts as verification. Do NOT ask them public knowledge (what is my phone number?). Choose something that is only known by a very small number of people (only them being the best). E.g Question: "When we went out for dinner the other day, what did you have for dessert? (one word, all lower case)". Answer: cheesecake.
This can be very annoying to get right, and that is one the of the prime reasons for Crypto Parties: because you are there and can just read each other's fingerprints. Or call out across the room "Ignore the question, just answer 'bill'". (i.e Question: "how many angels on the head of a pin?" Answer: bill).
You can see that it is not encrypted and click on the blue text to authenticate them.
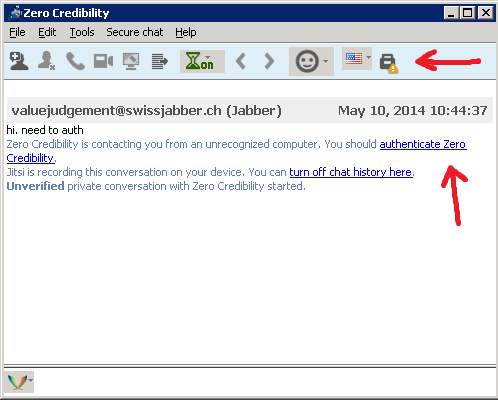

They respond
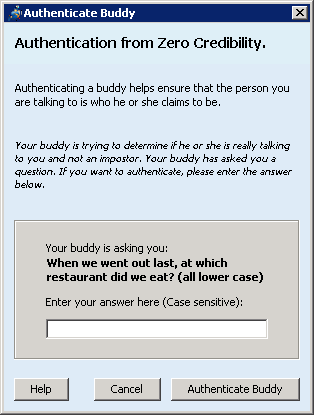
... and you see
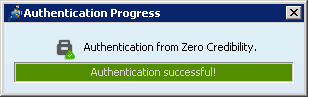
NOW you have a private conversation (green tick).
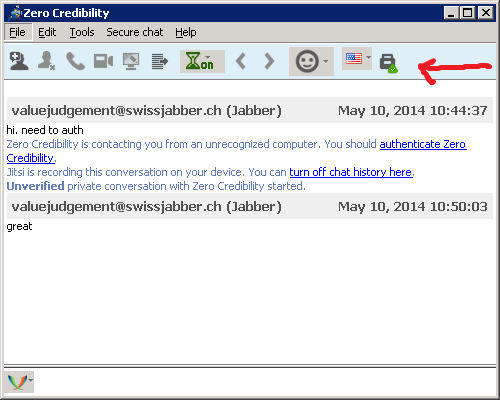
Now choose whether you wish to keep history for chats? You sent it over the wire encrypted. Do you want to keep a local plain text version? This is a question you should ask the OTHER PERSON!!
Finally, there are other 'nicer' chat tools, but you then have to add the crypto. Jitsi comes with it all by default, and more importantly can also do voice and video!!! But, you NEED headphones. It does not do feedback cancellation. Thus, when using a speaker the other person (and you) hear yourself as feedback.
You may consider this 'not as good as [other product]'. Perhaps it is a design choice. If you are using headphones the conversation is more secure than otherwise!!
2014-05-10, Copyright CC-BY-NC, DTU Environment
