How the NSA Plans to Infect ‘Millions’ of Computers with Malware
 One presentation outlines how the NSA
performs “industrial-scale exploitation” of computer networks across the
world.
One presentation outlines how the NSA
performs “industrial-scale exploitation” of computer networks across the
world.
Top-secret documents reveal that the National Security Agency is dramatically expanding its ability to covertly hack into computers on a mass scale by using automated systems that reduce the level of human oversight in the process.
The classified files – provided previously by NSA whistleblower Edward Snowden – contain new details about groundbreaking surveillance technology the agency has developed to infect potentially millions of computers worldwide with malware “implants.” The clandestine initiative enables the NSA to break into targeted computers and to siphon out data from foreign Internet and phone networks.
The covert infrastructure that supports the hacking efforts operates from the agency’s headquarters in Fort Meade, Maryland, and from eavesdropping bases in the United Kingdom and Japan. GCHQ, the British intelligence agency, appears to have played an integral role in helping to develop the implants tactic.
In some cases the NSA has masqueraded as a fake Facebook server, using the social media site as a launching pad to infect a target’s computer and exfiltrate files from a hard drive. In others, it has sent out spam emails laced with the malware, which can be tailored to covertly record audio from a computer’s microphone and take snapshots with its webcam. The hacking systems have also enabled the NSA to launch cyberattacks by corrupting and disrupting file downloads or denying access to websites.
The implants being deployed were once reserved for a few hundred hard-to-reach targets, whose communications could not be monitored through traditional wiretaps. But the documents analyzed by The Intercept show how the NSA has aggressively accelerated its hacking initiatives in the past decade by computerizing some processes previously handled by humans. The automated system – codenamed TURBINE – is designed to “allow the current implant network to scale to large size (millions of implants) by creating a system that does automated control implants by groups instead of individually.”
In a top-secret presentation, dated August 2009, the NSA describes a pre-programmed part of the covert infrastructure called the “Expert System,” which is designed to operate “like the brain.” The system manages the applications and functions of the implants and “decides” what tools they need to best extract data from infected machines.
Mikko Hypponen, an expert in malware who serves as chief research officer at the Finnish security firm F-Secure, calls the revelations “disturbing.” The NSA’s surveillance techniques, he warns, could inadvertently be undermining the security of the Internet.
“When they deploy malware on systems,” Hypponen says, “they potentially create new vulnerabilities in these systems, making them more vulnerable for attacks by third parties.”
Hypponen believes that governments could arguably justify using malware in a small number of targeted cases against adversaries. But millions of malware implants being deployed by the NSA as part of an automated process, he says, would be “out of control.”
“That would definitely not be proportionate,” Hypponen says. “It couldn’t possibly be targeted and named. It sounds like wholesale infection and wholesale surveillance.”
The NSA declined to answer questions about its deployment of implants, pointing to a new presidential policy directive announced by President Obama. “As the president made clear on 17 January,” the agency said in a statement, “signals intelligence shall be collected exclusively where there is a foreign intelligence or counterintelligence purpose to support national and departmental missions, and not for any other purposes.”
“Owning the Net”
The NSA began rapidly escalating its hacking efforts a decade ago. In 2004, according to secret internal records, the agency was managing a small network of only 100 to 150 implants. But over the next six to eight years, as an elite unit called Tailored Access Operations (TAO) recruited new hackers and developed new malware tools, the number of implants soared to tens of thousands.
To penetrate foreign computer networks and monitor communications that it did not have access to through other means, the NSA wanted to go beyond the limits of traditional signals intelligence, or SIGINT, the agency’s term for the interception of electronic communications. Instead, it sought to broaden “active” surveillance methods – tactics designed to directly infiltrate a target’s computers or network devices.
In the documents, the agency describes such techniques as “a more aggressive approach to SIGINT” and says that the TAO unit’s mission is to “aggressively scale” these operations.
But the NSA recognized that managing a massive network of implants is too big a job for humans alone.
“One of the greatest challenges for active SIGINT/attack is scale,” explains the top-secret presentation from 2009. “Human ‘drivers’ limit ability for large-scale exploitation (humans tend to operate within their own environment, not taking into account the bigger picture).”
The agency’s solution was TURBINE. Developed as part of TAO unit, it is described in the leaked documents as an “intelligent command and control capability” that enables “industrial-scale exploitation.”
TURBINE was designed to make deploying malware much easier for the NSA’s hackers by reducing their role in overseeing its functions. The system would “relieve the user from needing to know/care about the details,” the NSA’s Technology Directorate notes in one secret document from 2009. “For example, a user should be able to ask for ‘all details about application X’ and not need to know how and where the application keeps files, registry entries, user application data, etc.”
In practice, this meant that TURBINE would automate crucial processes that previously had to be performed manually – including the configuration of the implants as well as surveillance collection, or “tasking,” of data from infected systems. But automating these processes was about much more than a simple technicality. The move represented a major tactical shift within the NSA that was expected to have a profound impact – allowing the agency to push forward into a new frontier of surveillance operations.
The ramifications are starkly illustrated in one undated top-secret NSA document, which describes how the agency planned for TURBINE to “increase the current capability to deploy and manage hundreds of Computer Network Exploitation (CNE) and Computer Network Attack (CNA) implants to potentially millions of implants.” (CNE mines intelligence from computers and networks; CNA seeks to disrupt, damage or destroy them.)
Eventually, the secret files indicate, the NSA’s plans for TURBINE came to fruition. The system has been operational in some capacity since at least July 2010, and its role has become increasingly central to NSA hacking operations.
Earlier reports based on the Snowden files indicate that the NSA has already deployed between 85,000 and 100,000 of its implants against computers and networks across the world, with plans to keep on scaling up those numbers.
The intelligence community’s top-secret “Black Budget” for 2013, obtained by Snowden, lists TURBINE as part of a broader NSA surveillance initiative named “Owning the Net.”
The agency sought $67.6 million in taxpayer funding for its Owning the Net program last year. Some of the money was earmarked for TURBINE, expanding the system to encompass “a wider variety” of networks and “enabling greater automation of computer network exploitation.”
Circumventing Encryption
The NSA has a diverse arsenal of malware tools, each highly sophisticated and customizable for different purposes.
One implant, codenamed UNITEDRAKE, can be used with a variety of “plug-ins” that enable the agency to gain total control of an infected computer.
An implant plug-in named CAPTIVATEDAUDIENCE, for example, is used to take over a targeted computer’s microphone and record conversations taking place near the device. Another, GUMFISH, can covertly take over a computer’s webcam and snap photographs. FOGGYBOTTOM records logs of Internet browsing histories and collects login details and passwords used to access websites and email accounts. GROK is used to log keystrokes. And SALVAGERABBIT exfiltrates data from removable flash drives that connect to an infected computer.
The implants can enable the NSA to circumvent privacy-enhancing encryption tools that are used to browse the Internet anonymously or scramble the contents of emails as they are being sent across networks. That’s because the NSA’s malware gives the agency unfettered access to a target’s computer before the user protects their communications with encryption.
It is unclear how many of the implants are being deployed on an annual basis or which variants of them are currently active in computer systems across the world.
Previous reports have alleged that the NSA worked with Israel to develop the Stuxnet malware, which was used to sabotage Iranian nuclear facilities. The agency also reportedly worked with Israel to deploy malware called Flame to infiltrate computers and spy on communications in countries across the Middle East.
According to the Snowden files, the technology has been used to seek out terror suspects as well as individuals regarded by the NSA as “extremist.” But the mandate of the NSA’s hackers is not limited to invading the systems of those who pose a threat to national security.
In one secret post on an internal message board, an operative from the NSA’s Signals Intelligence Directorate describes using malware attacks against systems administrators who work at foreign phone and Internet service providers. By hacking an administrator’s computer, the agency can gain covert access to communications that are processed by his company. “Sys admins are a means to an end,” the NSA operative writes.
The internal post – titled “I hunt sys admins” – makes clear that terrorists aren’t the only targets of such NSA attacks. Compromising a systems administrator, the operative notes, makes it easier to get to other targets of interest, including any “government official that happens to be using the network some admin takes care of.”
Similar tactics have been adopted by Government Communications Headquarters, the NSA’s British counterpart. As the German newspaper Der Spiegel reported in September, GCHQ hacked computers belonging to network engineers at Belgacom, the Belgian telecommunications provider.
The mission, codenamed “Operation Socialist,” was designed to enable GCHQ to monitor mobile phones connected to Belgacom’s network. The secret files deem the mission a “success,” and indicate that the agency had the ability to covertly access Belgacom’s systems since at least 2010.
Infiltrating cellphone networks, however, is not all that the malware can be used to accomplish. The NSA has specifically tailored some of its implants to infect large-scale network routers used by Internet service providers in foreign countries. By compromising routers – the devices that connect computer networks and transport data packets across the Internet – the agency can gain covert access to monitor Internet traffic, record the browsing sessions of users, and intercept communications.
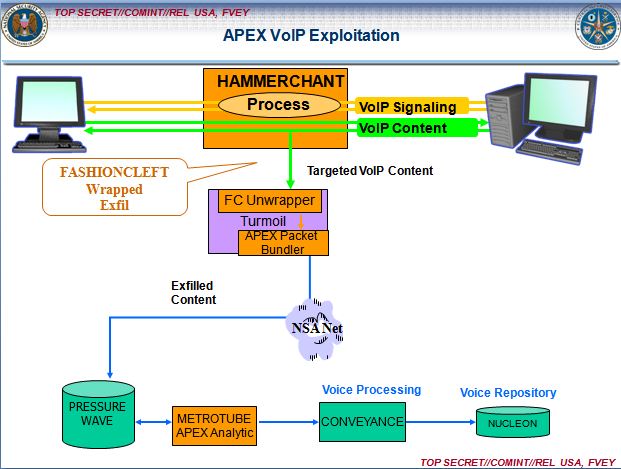
Two implants the NSA injects into network routers, HAMMERCHANT and HAMMERSTEIN, help the agency to intercept and perform “exploitation attacks” against data that is sent through a Virtual Private Network, a tool that uses encrypted “tunnels” to enhance the security and privacy of an Internet session.
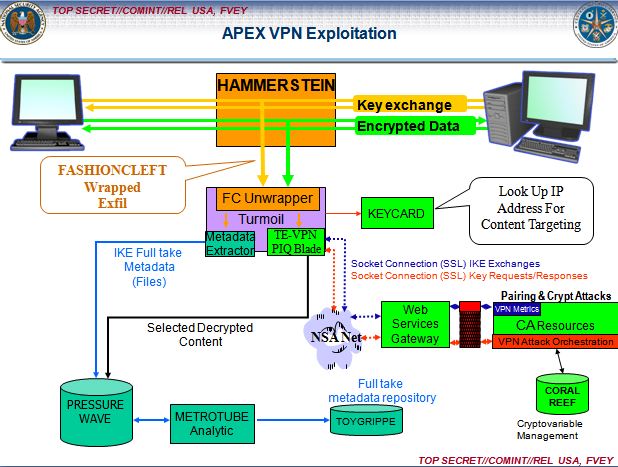
The implants also track phone calls sent across the network via Skype and other Voice Over IP software, revealing the username of the person making the call. If the audio of the VOIP conversation is sent over the Internet using unencrypted “Real-time Transport Protocol” packets, the implants can covertly record the audio data and then return it to the NSA for analysis.
But not all of the NSA’s implants are used to gather intelligence, the secret files show. Sometimes, the agency’s aim is disruption rather than surveillance. QUANTUMSKY, a piece of NSA malware developed in 2004, is used to block targets from accessing certain websites. QUANTUMCOPPER, first tested in 2008, corrupts a target’s file downloads. These two “attack” techniques are revealed on a classified list that features nine NSA hacking tools, six of which are used for intelligence gathering. Just one is used for “defensive” purposes – to protect U.S. government networks against intrusions.
“Mass exploitation potential”
Before it can extract data from an implant or use it to attack a system, the NSA must first install the malware on a targeted computer or network.
According to one top-secret document from 2012, the agency can deploy malware by sending out spam emails that trick targets into clicking a malicious link. Once activated, a “back-door implant” infects their computers within eight seconds.
There’s only one problem with this tactic, codenamed WILLOWVIXEN: According to the documents, the spam method has become less successful in recent years, as Internet users have become wary of unsolicited emails and less likely to click on anything that looks suspicious.
Consequently, the NSA has turned to new and more advanced hacking techniques. These include performing so-called “man-in-the-middle” and “man-on-the-side” attacks, which covertly force a user’s internet browser to route to NSA computer servers that try to infect them with an implant.
To perform a man-on-the-side attack, the NSA observes a target’s Internet traffic using its global network of covert “accesses” to data as it flows over fiber optic cables or satellites. When the target visits a website that the NSA is able to exploit, the agency’s surveillance sensors alert the TURBINE system, which then “shoots” data packets at the targeted computer’s IP address within a fraction of a second.
In one man-on-the-side technique, codenamed QUANTUMHAND, the agency disguises itself as a fake Facebook server. When a target attempts to log in to the social media site, the NSA transmits malicious data packets that trick the target’s computer into thinking they are being sent from the real Facebook. By concealing its malware within what looks like an ordinary Facebook page, the NSA is able to hack into the targeted computer and covertly siphon out data from its hard drive. A top-secret animation demonstrates the tactic in action.
The documents show that QUANTUMHAND became operational in October 2010, after being successfully tested by the NSA against about a dozen targets.
According to Matt Blaze, a surveillance and cryptography expert at the University of Pennsylvania, it appears that the QUANTUMHAND technique is aimed at targeting specific individuals. But he expresses concerns about how it has been covertly integrated within Internet networks as part of the NSA’s automated TURBINE system.
“As soon as you put this capability in the backbone infrastructure, the software and security engineer in me says that’s terrifying,” Blaze says.
“Forget about how the NSA is intending to use it. How do we know it is working correctly and only targeting who the NSA wants? And even if it does work correctly, which is itself a really dubious assumption, how is it controlled?”
In an email statement to The Intercept, Facebook spokesman Jay Nancarrow said the company had “no evidence of this alleged activity.” He added that Facebook implemented HTTPS encryption for users last year, making browsing sessions less vulnerable to malware attacks.
Nancarrow also pointed out that other services besides Facebook could have been compromised by the NSA. “If government agencies indeed have privileged access to network service providers,” he said, “any site running only [unencrypted] HTTP could conceivably have its traffic misdirected.”
A man-in-the-middle attack is a similar but slightly more aggressive method that can be used by the NSA to deploy its malware. It refers to a hacking technique in which the agency covertly places itself between computers as they are communicating with each other.
This allows the NSA not only to observe and redirect browsing sessions, but to modify the content of data packets that are passing between computers.
The man-in-the-middle tactic can be used, for instance, to covertly change the content of a message as it is being sent between two people, without either knowing that any change has been made by a third party. The same technique is sometimes used by criminal hackers to defraud people.
A top-secret NSA presentation from 2012 reveals that the agency developed a man-in-the-middle capability called SECONDDATE to “influence real-time communications between client and server” and to “quietly redirect web-browsers” to NSA malware servers called FOXACID. In October, details about the FOXACID system were reported by the Guardian, which revealed its links to attacks against users of the Internet anonymity service Tor.
But SECONDDATE is tailored not only for “surgical” surveillance attacks on individual suspects. It can also be used to launch bulk malware attacks against computers.
According to the 2012 presentation, the tactic has “mass exploitation potential for clients passing through network choke points.”

Blaze, the University of Pennsylvania surveillance expert, says the potential use of man-in-the-middle attacks on such a scale “seems very disturbing.” Such an approach would involve indiscriminately monitoring entire networks as opposed to targeting individual suspects.
“The thing that raises a red flag for me is the reference to ‘network choke points,’” he says. “That’s the last place that we should be allowing intelligence agencies to compromise the infrastructure – because that is by definition a mass surveillance technique.”
To deploy some of its malware implants, the NSA exploits security vulnerabilities in commonly used Internet browsers such as Mozilla Firefox and Internet Explorer.
The agency’s hackers also exploit security weaknesses in network routers and in popular software plugins such as Flash and Java to deliver malicious code onto targeted machines.
The implants can circumvent anti-virus programs, and the NSA has gone to extreme lengths to ensure that its clandestine technology is extremely difficult to detect. An implant named VALIDATOR, used by the NSA to upload and download data to and from an infected machine, can be set to self-destruct – deleting itself from an infected computer after a set time expires.
In many cases, firewalls and other security measures do not appear to pose much of an obstacle to the NSA. Indeed, the agency’s hackers appear confident in their ability to circumvent any security mechanism that stands between them and compromising a computer or network. “If we can get the target to visit us in some sort of web browser, we can probably own them,” an agency hacker boasts in one secret document. “The only limitation is the ‘how.’”
Covert Infrastructure
The TURBINE implants system does not operate in isolation.
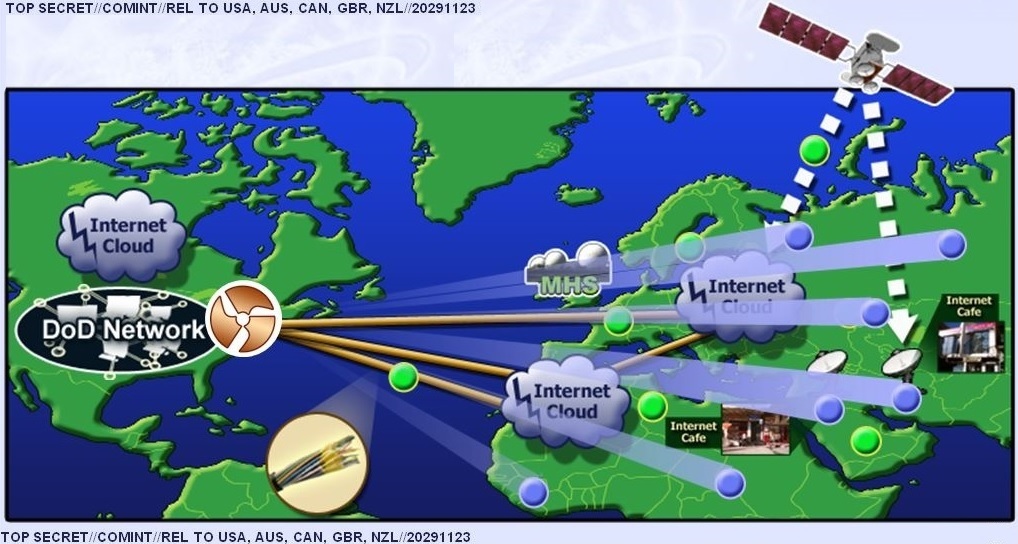
It is linked to, and relies upon, a large network of clandestine surveillance “sensors” that the agency has installed at locations across the world.
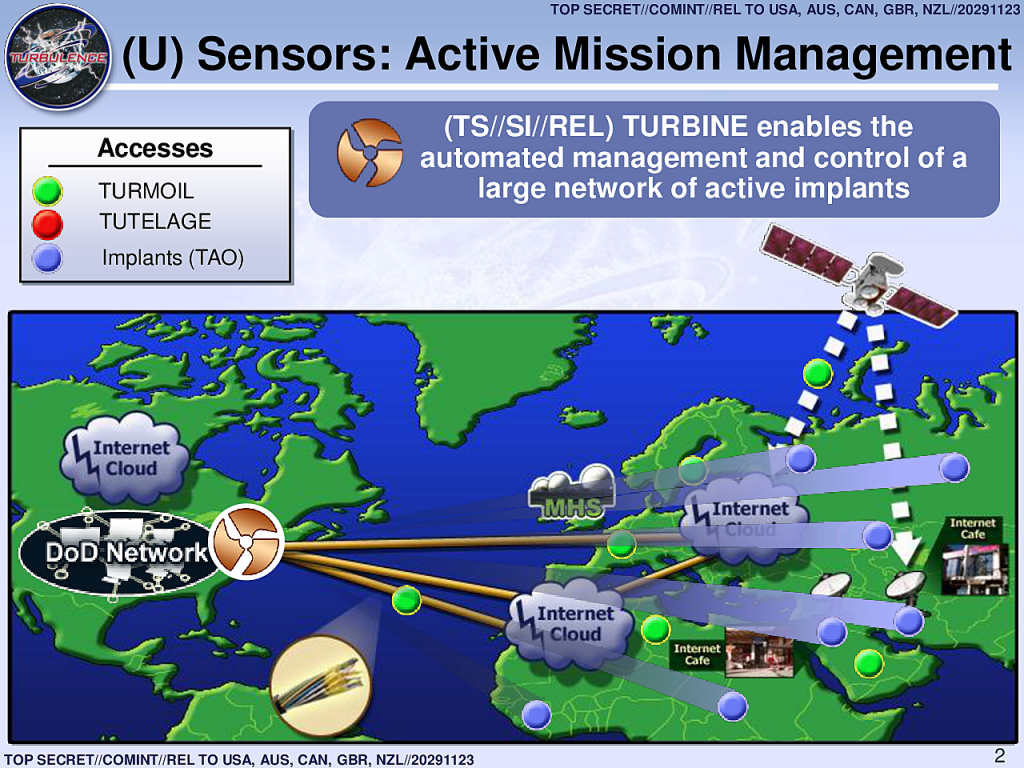
The NSA’s headquarters in Maryland are part of this network, as are eavesdropping bases used by the agency in Misawa, Japan and Menwith Hill, England.
The sensors, codenamed TURMOIL, operate as a sort of high-tech surveillance dragnet, monitoring packets of data as they are sent across the Internet.
When TURBINE implants exfiltrate data from infected computer systems, the TURMOIL sensors automatically identify the data and return it to the NSA for analysis. And when targets are communicating, the TURMOIL system can be used to send alerts or “tips” to TURBINE, enabling the initiation of a malware attack.
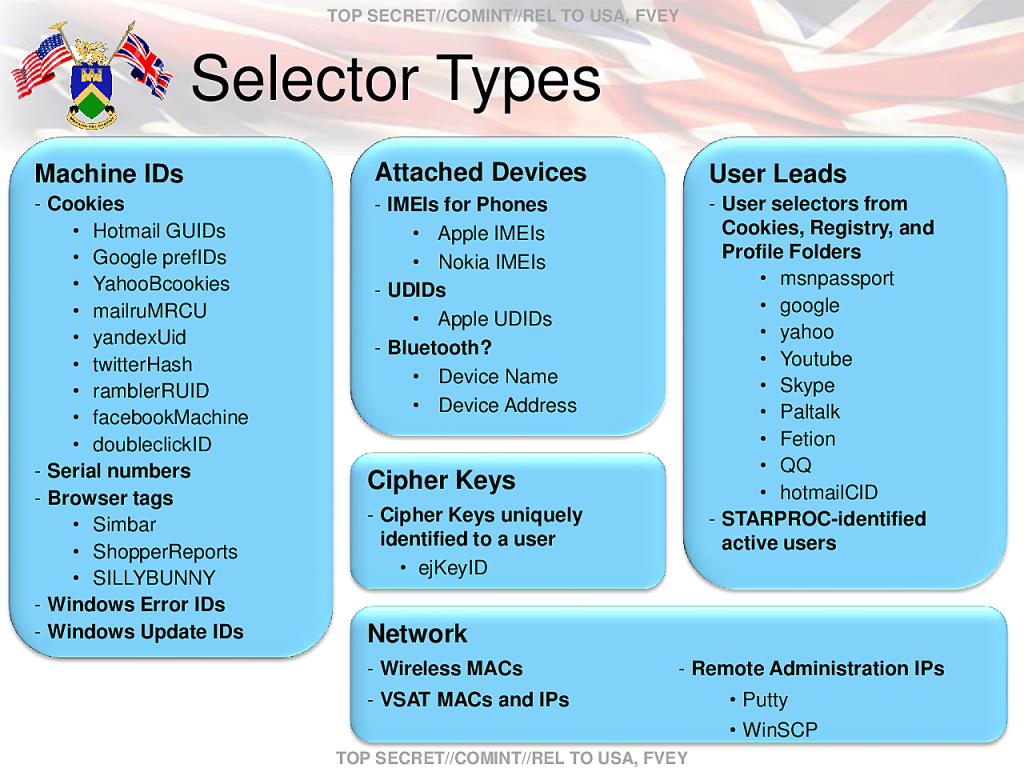
The NSA identifies surveillance targets based on a series of data “selectors” as they flow across Internet cables. These selectors, according to internal documents, can include email addresses, IP addresses, or the unique “cookies” containing a username or other identifying information that are sent to a user’s computer by websites such as Google, Facebook, Hotmail, Yahoo, and Twitter.
Other selectors the NSA uses can be gleaned from unique Google advertising cookies that track browsing habits, unique encryption key fingerprints that can be traced to a specific user, and computer IDs that are sent across the Internet when a Windows computer crashes or updates.
What’s more, the TURBINE system operates with the knowledge and support of other governments, some of which have participated in the malware attacks.
Classification markings on the Snowden documents indicate that NSA has shared many of its files on the use of implants with its counterparts in the so-called Five Eyes surveillance alliance – the United Kingdom, Canada, New Zealand, and Australia.
GCHQ, the British agency, has taken on a particularly important role in helping to develop the malware tactics. The Menwith Hill satellite eavesdropping base that is part of the TURMOIL network, located in a rural part of Northern England, is operated by the NSA in close cooperation with GCHQ.
Top-secret documents show that the British base – referred to by the NSA as “MHS” for Menwith Hill Station – is an integral component of the TURBINE malware infrastructure and has been used to experiment with implant “exploitation” attacks against users of Yahoo and Hotmail.
In one document dated 2010, at least five variants of the QUANTUM hacking method were listed as being “operational” at Menwith Hill. The same document also reveals that GCHQ helped integrate three of the QUANTUM malware capabilities – and test two others – as part of a surveillance system it operates codenamed INSENSER.
GCHQ cooperated with the hacking attacks despite having reservations about their legality. One of the Snowden files, previously disclosed by Swedish broadcaster SVT, revealed that as recently as April 2013, GCHQ was apparently reluctant to get involved in deploying the QUANTUM malware due to “legal/policy restrictions.” A representative from a unit of the British surveillance agency, meeting with an obscure telecommunications standards committee in 2010, separately voiced concerns that performing “active” hacking attacks for surveillance “may be illegal” under British law.
In response to questions from The Intercept, GCHQ refused to comment on its involvement in the covert hacking operations. Citing its boilerplate response to inquiries, the agency said in a statement that “all of GCHQ’s work is carried out in accordance with a strict legal and policy framework which ensures that our activities are authorized, necessary and proportionate, and that there is rigorous oversight.”
Whatever the legalities of the United Kingdom and United States infiltrating computer networks, the Snowden files bring into sharp focus the broader implications. Under cover of secrecy and without public debate, there has been an unprecedented proliferation of aggressive surveillance techniques. One of the NSA’s primary concerns, in fact, appears to be that its clandestine tactics are now being adopted by foreign rivals, too.
“Hacking routers has been good business for us and our 5-eyes partners for some time,” notes one NSA analyst in a top-secret document dated December 2012. “But it is becoming more apparent that other nation states are honing their skillz [sic] and joining the scene.”
———
Documents published with this article:
- Menwith Hill Station Leverages XKeyscore for Quantum Against Yahoo and Hotmail
- Five Eyes Hacking Large Routers
- NSA Technology Directorate Analysis of Converged Data
- Selector Types
- There Is More Than One Way to Quantum
- NSA Phishing Tactics and Man in the Middle Attacks
- Quantum Insert Diagrams
- The NSA and GCHQ’s QUANTUMTHEORY Hacking Tactics
- TURBINE and TURMOIL
- VPN and VOIP Exploitation With HAMMERCHANT and HAMMERSTEIN
- Industrial-Scale Exploitation
- Thousands of Implants


NSA Domestic Surveillance Began 7 Months Before 9/11, Convicted Qwest CEO Claims BY RYAN SINGEL 10.11.07
http://www.wired.com/threatlevel/2007/10/nsa-asked-for-p/
You want spyfree communications FREE?
There you go: https://unseen.is
Ensure Your Privacy. Secure Your Freedom.
Hey kids! Ever wanna know how your government keeps you little dopes safe? Well your pal, the NSA, has provided this fun little cartoon with the grownup name, “Active Mission Management”, that explains it all !
First, you see the big black bubble with the funny-looking stuff inside? Well, kids, that’s the protection sphere that covers most of the good old USA – with the exception of Florida, which will be an underwater park in 50 years; and California, which we’re not really sure is part of America anyway. So if you live in the permanent part of the country, this bubble keeps you safe from terrorists by watching everything you do so you won’t get hurt. Isn’t that great !?
But that’s not all your pals at the NSA do for ya, kids! We also have this supersecret windmill thingy called a ‘turbine’, that we use to suck up viruses from the cool-looking ‘Internet Cloud’ that we placed over Canada. It’s kinda complicted, we don’t want to confuse you with a lot of big words, but basically it works like this:
The lightning coming from the cloud over Canada heats up the tar sands and releases ancient mastodon viruses that have been sleeping in the soil. These anti-terror bugs are swept up by the giant windmill floating over Boston, which blasts them across the Atlantic Ocean to be eaten by terrorist computers in places we don’t like. The left-over viruses form huge clouds which hover over trouble spots like the continents of Africa and Europe. Neat, huh kids ?
But that’s not all we do to keep you darlings safe so you can focus on the important things in life, like making lots and lots of money! The turbine also sends out cute little blue balls we like to call ‘implants’. (Now, for you teenage boys out there – these are NOT the silicone things that make Ms Jones down the block the envy of the neighborhood!). These are ‘magic bubbles’ which penetrate deep down into the roots of dirty governments, leaving them ‘squeaky-clean’ of any information that makes us look bad. We also secretly installed lime-green ‘turmoil’ buttons in places with ‘bad actors’. They look just like bushes, but we can make them spin real fast to cause disasters, like tornados and hurricanes, when people criticize our President. You can bet things are pretty windy out there these days, kids!
But don’t you worry, ’cause, best of all, there’s this gigantic satellite parked way up north that shoots death rays at evil jerks like Finland, and one of those former USSR countries whose name we can’t pronounce but we’ll probably be at war against soon. Isn’t that great ?!
And to keep anyone else from messing around with your God-given American Rights, we put some big domes over England so they can’t look out. Those guys are a bunch of Sneaky Peepers !
Well, we sure hope this helps, and remember, kids: Your friends at the NSA are always “Lyin’ & Spyin so we can protect you little dumb buggers from Dyin’ ” !
You’re welcome.
fuck the NSA, come get my data bitches. I dare you!
Last time I checked, it was illegal to purposely infect another persons computer with any form of virus or any program designed to “Over take, control or otherwise corrupt files”.
Remember that popular saying. They dont need to kill you, they just need you to think that they can kill you
This is not COLLECTING data. This is an obstruction of justice. The NSA is probably responsible for 100s of million of dollars in damage to hardware, loss of income resulting in computer problems associated with their malware. Inconvenience of your computer acting up or slowed, even causing programs not to function as with a virus. There is no telling what damage this does and they will take no accountability for it. There is no way they need to collect info on millions of people unless there is a evil agenda at hand. I say shut therm down all together. Clear abuse of power no telling for how long and how invasive. You can bet they listen in on insider trading, business deals, investment type stuff totally unrelated to security, if anything they are the criminals and use the information for money and control. I had enough of a bunch of people who I dont know doing this crap on all levels. If anyone I donot know is lurching into my computer for any reason is an ENEMY, any one using this info is criminal. Appropriate measures need to be taken to ELIMINATE these enemies and if need be departments.
So they have hacked into all these computers? Did they learn anything useful?
I have said for years, that EVERY AMERICAN should upset, because they are ALL CONSIDERED TERRORISTS by the government!!!!!!!!!
How does that make you feel?
As the government gets PAID for SPYING ON YOU?
If Americans do not GET ORGANIZED – forget your FREEDOM and LIBERTY,,,
It will be up to the younger generation to wake up and take charge
This is precisely why I don’t deal with social networks. Sites that require logging in to comment, HuffPost, for example are unfair to the average commenter.
Yep! they already done it to my computer through Facebook & Yahoo. I DISCOVERED this before Snodwen blew the whistle. Its best not to participate on Facebook anyway or continue as if nothing is happening because the damage to our constitution is already done thanks to Bush & Obama under the direction of the evil Dick Cheney, the monster who is not a human.
FYI
ok, and this is only half tongue-in-cheek sadly…..
But the only real solution at this point would be to create an entirely new nation somewhere that is literally Luddite and agrarian, and let the rest of the world self destruct. The only way to keep anyone from listening to your phone conversations is to NOT have phone conversations. Want them to stop monitoring your computer activity… disconnect from the web entirely and never get back on it… ironic considering the forum I am posting this on huh. We allowed this to happen now its up to us to stop it. And to be completely honest, I am not sure it can be stopped at this point. We have given birth to a monster and it is called the government.
Let’s be honest, we DO need some level of government, but the people need to be in control of the government not the other way around. The true purpose of government is to protect the people it serves not to control them. Not to spy on them. And certainly not to create situations that cause their people to distrust them.
Believe it or not I really am a patriot. I love my country (U.S.A. to be clear). But no, I haven’t trusted the government for a long time now. Look at what they did in the past.
McCarthyism, the C.I.A. (lol sorry had to take that shot spooks), Hoover, and don’t forget what the research on nuclear power turned into (remember those 2 bombs that got dropped on Japan?), and these are just off the top of my head…. Had to peek under my tinfoil hat to find them but they were there.
Do I sound like a conspiracy theorist, probably. does that mean I am wrong? No. We all have heard the saying “Just because I am paranoid, it doesn’t mean they are NOT out to get me.”
Now I am sure just typing this post has probably landed me on some kind of list somewhere, and that’s before I even uploaded it to the web. Do I care? No, let them hack my computer. The worst they will find on it is some internet pron, and last time I checked that was still legal. Otherwise I play video games and study for school with it. Yeah that makes me a big threat. So go ahead and waste time and money hacking me, oh, and when you get to that picture of me flipping off the camera… that one is for you. Enjoy.
Sincerely,
The Founding Member of the
“Tinfoil Apocalypse Society”
If “they” decide to hack your computer (not a likely individualized target, of course), they will “find” whatever is most useful for them to find, and your “I don’t know how that got there!” protestations will be quite futile.
Exactly!
Shane, the problem is NSA false positives not NSA snooping; that is, when the NSA says you are a terrorists when you are not. The odds of false positives are very high when you snoop on 300 million people (see Bayes Theorem for example to calculate the odds, or just look at the 800,000 “terrorists” on the no fly list). Then, when they falsely accuse you how will you protect yourself; no courts, secret evidence, no warrants, no habeus corpus rights.
Bunch of bastards!
They can have at it,but they will be bored to death if they infect mine.
to all that is concerned cancel your internet and your cell phone all companies you pay to protect your ID all these people will suffer no need for them with no internet no need for new computer etc. high unemployment no taxes for the government.that’s the only way to stop it.a total internet shut down and not just unplugging the machine.how much money would these governments loose in one second.just a thought nsa
Where do you think Facebook located their mysterious investors . . . if you believe the whole Facebook story?
If you need better security, drop the need for real-time connectivity. Go back to the Bulletin Board System Store-and-Forward model. Do your encryption offline, Abandon ‘browsing the web” and similar online uses for the systems you use to communicate sensitive data with. Shut down all server ports, configure a hardware firewall to allow no incoming requests. Install a secure system like SELINUX and use it in batch-comm mode only. Most of the risk exposure in Windows-style systems inheres in the desire for realtime connectivity. Use UUCP (Unix-to-Unix Copy) to exchange only 7-bit textfiles, (use uuencode/uudecode to transmit necessary binary data, but avoid executables.)
The first decade of the internet provides us a model for secure network comms, and we can still use it. The BBS culture that preceeded it provides us a model for networks which the government cannot monitor, because access can be controlled, and connetivity limited. Of course, any system can be penetrated, but stepping back to an earlier network model defeats this automated penetration strategy and requires a human involvement.
For encryption? Write your own, make it simple and robust, avoid the algebraic substitutions the government pushes. One pretty easy method is bitwise-transposition. You can write one in C in a day, and
nothing short of key theft or traffic analysis can attack it productively. I call mine Brainworm BTK (bitwise transposition kludge. Unlike Triple DES, etc, it has only one “bad” passphrase: all letters identical.) Like all ramifications of the One Time Pad, it’s unbreakable, and unlike most ciphers, bits have no individual characters, so there are fewer tools for cryptanalyzing a message.
There’s nothing hard about security, other than making sure everybody adheres to good protocols.
That, historically, is impossible.
I LIKE
IS VERY GOOD IDEA
I got spyware installed in my computer by a Linked-In connection invitation by a “Major Slaughter.”
That these people have gone to these breathtaking extents to collect mass data on innocent Americans is quite shocking. Personal data collected by the US Govt. thru the IRS alone is a good example of how the US Govt. has and will continue to use such information to target individuals, groups & businesses for harassment, abuse and other criminally-motivated retaliation against political enemies. Presidents Johnson, Nixon, Clinton and both Bushes did it when in office. To say that this new batch of personal data will not be equally exploited by Obama or other rogue Govt. agents is to live in a fantasy world of disbelief, or the fantasy world of sports, gaming, and internet trash that is actually “digital addiction” and idol worship that always results in self-delusion, and vulnerability, and societal self-destruction.
Never forget, that the internet was originally developed, by DARPA (Defense Advanced Research Projects Agency). As such, Everything should be suspect, as far as surveillance, on the internet, goes.
Never think, for any reason, that your computer usage is anonymous . Even when using certain so called ‘anonymous’ tech. products.
Always assume that Everything that you say or do, on Any electronic device, is subject to governmental snooping. That includes your old fashion telephone calls.
The TV show ‘Person of Interest’, may very well be a vision of the future, but if someone can imagine it, then it will happen, sooner or later… and in today’s ever accelerating technical world, sooner is a better bet !
Let them try to get their spyware past my realtime MBAM spyware monitor!
basically… do some research on gap jumping, bad bios (which was a fake based on the real thing that does the same thing) and some of the tools at their disposal. They could overpower your network interface, they have access to MBAM source code i mean…all they have to do is be within 8 miles of your home and they can have access whenever they want. they can upload custom firmware into your hard drive…currently there are -no- antivirus databases that scan firmware.
As if they havent already bought out MBAM
smooth statement you idiot… by the time you posted that they already had.
Be sure that MBAM won’t stop their spyware. I’ve been targeted by these rogue agencies, meaning I’ve been hacked (PC and samrtphone) and then after formatting my PC, targeted again (it was a clear targeted attack through trojans sent by emails), I pass them on VIRUS TOTAL detection, only 2 or 3 antiviruses detected them, and MBAM was not among them !
Dude, they’re the freaking NSA. I’m sure they can get passed some anti-malware somehow. The article stated that they can customize their malware tools pretty much however they want.
LOL! good luck with that.
Does this really surprise anyone ? If it does then it’s your own fault .
Wars no longer surprise me, floods no longer surprise me and famine no longer surprises me. Does this mean that I’m total disinterested in anything that happens? No, because being surprised is not the only worthy goal in life.
Yea I’ve never understood that criticism. I suppose if they dod find actual irrefutable proof that the CIA killed Kennedy there would be people complaing “This isn’t news, we knew that all along, move on.”
We have always been and remain very quick to jump onto any reason to blame the federal government, whether right or wrong. This is because the Federal government has been caught lying multiple times. I’m beginning to believe we should ignore the Feds and work on changing things at a State level…or ask Gene Sharp, founder of the Albert Einstein Institution and Nobel Peace Prize nominee.
What bothers me most about the data collection is actually not the data collection, per se, but in the potential for abuse of the knowledge gleaned from the data. If Snowden, a contractor for a 3rd party IT company can get his hands on all this stuff, how many other’s have already done it – not for the noble purpose of exposing it all – but for their own personal enrichment, or to fuck somebody over, blackmail, extortion, or whatever. How many ideas have been stolen and sold to competing companies? How much insider trading on wall street has occurred as a result of this data collection? It’s simply too tempting for mortals to have all this data sitting there for the perusal. And the idea that we should trust this data to for-profit 3rd party enterprises is terrifying and IMHO a serious failure in judgement by NSA.
What I find hard to understand is that with all this amazing kit they still can’t put together a nice looking powerpoint. It looks like they’ve done it in MS paint…
powerpoint is actually a virus.
Why don’t America quit using computers and cell phones…!@ Then they can only spy on each other again,,,,Why do you think everybody can get a computer or cell phone so easily… silly…they can’t spy on you if you don’t have their inventions to see you with…!!!! Come on…yal’ ain’t that stupid…are you????
You are a very smart lady !
GLENN GREENWALD will go down in history as A TOTAL HERO.
The only way to take on this illegal activity is public awareness.
Congratulations Glenn.
I don’t know about that dude. We’ve been pretty aware of a lot of their spy efforts (thanks to Edward Snowden) and they haven’t stopped yet. Public awareness certainly does help, but it isn’t enough.
John Mcafee on infowars today…is another one… don’t miss it !!!
Is it possible to download these files? Once upon time you could find all these leaks, but now. It look like a few chosen can see it…
Any thing you here about me is just BS. Most of my life has been documented in Government files already. Anything else they want to know, just ask me. If you get info from from Facebook, I consider it bad info written by others to under-mind my life. And what my grand-kids write about me on their sites are just BS, too!
A lot of things have been written about me for my words about articles. I’m now a racist. Funny that they never knew my friends in the Air Force and other major metropolitan areas in the US. A lot of different races of people from Afro-American to native American. To those who doubt it, check with the NSA. I got a good record. And to others, go SUCK A POST!!! With all my love,… ME!
TIA, or Total Information Awareness has been the policy of this government for a long, long time. Nothing in these documents are all that surprising actually. Every single node on the Internet is owned – be it a router, a windows/mac/linux box/smartphone – all of them. Accessible at any time, and the full functionality of each device is available. Why do you think all smartphoens have cameras and gps devices? Seriously. Backbone routers are compromised to strip the exfiltrated packet-padding data appended to legitimate traffic sent from compromised nodes (e.g. you) and is shunted to massive databases for automated analysis. This is NOT news. Encryption is pointless because the node itself is compromised. As a normal, non-threat entity, the best you can hope for is that they don’t inadvertently fuck up your box or delete anything important! If you are connected, you are completely laid bare. Period. Stop acting indignant or surprised. Jeez.
You are exactly right, for anyone who thinks this is all a new revelation hasn’t been paying attention. Its not so much intriguing how these folks do this, more so than how long they have been doing it for without really anyone calling them out.
Snowden is no hero and some of this stuff should never have been made public. I find it interesting to see how this is all interfaced with literally everything.
This is deeply disturbing that our own Govt. deems it necessary to engage in these types of actions to spy on innocent Americans and others abroad. The lust for power and the lust of possessing it are always dangerous and end up with the suffering of millions of average people just trying to live and survive for a better day. This whole scheme by the USA Govt. and NSA can only inspire hatred of the USA. And they will say that with so many freedoms that Americans are at fault for letting their Govt. get out of control. So the blame carries over to all Americans and only gets worse when the retaliation and spirit of revenge rears their ugly heads.
For those that keep stating “Americans”, remember that these documents and operations were carried out by other organizations as well. GCHQ is one. But look at the letters at the bottom of the docs. It’s not just the US and GB.
At what point in time did It become legal to invade peoples privacy on their phone calls and emails without a warrant from a judge. I think a class action lawsuit against the Federal Government is what is needed.
“At what point in time did It become legal to invade peoples privacy on their phone calls and emails without a warrant from a judge.”
At the time we lost the concept of limited government. I’m not sure when but it just sort of slipped away by subtle degrees.
no shit, how do we do that. i’m all about protecting us from terrorist and shit but this is going after the people and they got no right doing that. they have no right listening to my computer mic or viewing my webcam. i’m not a threat to them and most people are not. they need to get there priority’s right
We’d be spinning against a hurricane. Do you not think that the Justice Department is not privy to all of this?
Patriot Act
Time to revisit September 11, 2001. Wasn’t that the alleged reason for the “War on Terror” and the “Patriot Act?”
At least the implants were not penile implants.
This site is not encrypted.
Amerika=4th REICH
Trust me.
It isn’t going to last one thousand years.
4th Reich, this exactly what i say about the US gov for 15 years now.
What a dirty filthy f EVIL REGIME AMERIKA IS..
as some commenters have mentioned before – the situation is deeply ironic – as the only realistic way to fight the ever increasing intrusion -(mainly by private enterprises) – is – first – to get out of social media – and then out of the Internet entirely – and as getting out of facebook -(even if it was very difficult) – was such a satisfying experience to unplug from the Internet might be even better?
-(with one exception – one needs to keep the contact with tehe economical thoughts of Paul Krugman)
But everything else? –
Let it go guys – It’s not worth it!
-(and what is the evil facebook reference doing on the right top of this comment section?)
-(and what is this evil little facebook sign on top of this page?)
The thing that one needs most to let go of is the operating system which allows other people to take control of it. I am deeply disappointed that this article does not make that crystal clear. Much of the problem here is with MS Windows allowing operation without a password. I’m not advocating any specific OS, but if a computer is able to run a virus without the operator allowing it, then there is something seriously wrong. I run UNIX systems in my home, (cost nothing) but others may prefer any of the many other choices out there. So, the article should say “Windows Computer”, and not “computer”. People have a choice and it is wrong to suggest that they don’t. Does the author have shares in Microsoft? It looks like it.
The National Security Agency – NSA – is an integral part of United States Department of Defense. Its facilities are military installations.
Why does this need to be stressed?
Because these covert operations are reaching almost every computer and mobile phone user on this planet. And these operations have been conducted by the US military.
if someone didn’t get it yet, it means every person (with internet connection or a person with a sim-card) in the world is a direct target for abuse by the US military.
No one is safe from their bombs.
No one is safe from their electronic attacks.
What do you mean? Let us all shun all internet. I can’t imagine what way US is watching me, you and billion others. I doubt US govt might have sponsored Facebook’s Whatsapp purchase to snoop more millions netizens. Courtesy Obama, who claimed to be a champion of free speech and democracy. Certainly biggest hacker in the world turned out to be US led by its trophy president. And add to it, Google, Facebook (Cohorts in snooping mega-scheme) are planning Drones and Loons so that it can facilitate US to reach the unreachable corners of the world. Now US can watch how African aboriginals copulate, live. What a fun? Strange enough few Americans are complaining. Though EU is at the receiving end now, and asking for tougher measures, I wonder does EU have spine take US head on.
What do you mean? Let us all shun all internet. I can’t imagine what way US is watching me, you and billion others. I doubt US govt might have sponsored Facebook’s Whatsapp purchase to snoop more millions netizens. Courtesy Obama, who claimed to be a champion of free speech and democracy. Certainly biggest hacker in the world turned out to be US led by its trophy president. And add to it, Google, Facebook (Cohorts in snooping mega-scheme) are planning Drones and Loons so that it can facilitate US to reach the unreachable corners of the world. Now US can watch how African aboriginals copulate, live. What a fun? Strange enough few Americans are complaining. Though EU is at the receiving end now, and asking for tougher measures, I wonder does EU have spine take US head on.
ask the NSA what part they had on the attack of THE USS LIBERTY THE DEATH OF 34 AMERICAN SAILORS AND THE CAPTURE OF THE USS PUEBLO?
Wow, what a surprise! Said not a single American.
My first comment didn’t appear here. Is it firstlook or NSA?
A week or so ago I posted a video, which is strongly critical of the status quo, on my wordpress blog. Then opened a second tab in firefox to check the page. Nothing appeared!
Refreshed both tabs several times. The video appeared on the page in the original tab but not on the new tab for at least 15 minutes.
This can only occur if there are two identical blog sites under my name, one of which isn’t controlled by yours truly.
If your living right why do you care, the government doesn’t care about your porn, if your not a criminal they won’t give a shit about you, they are not interested in watching you masturbate, everybody that’s worried and mad seems like they are doing something wrong that they wan’t to hide.
Yeah, I mean, just like the gov has done nothing wrong and is embracing and welcoming the wholesale exposure of it’s activities, we should have no problem with massive, unfettered and indescriminate spying of our private activities. lol
Exactly
Well they seem to care about journalists, activists and protesters, and minority groups, and none of these are criminal activities. Also what about businesses intellectual property, is that not important ? But hey yeah right Blake, we must all be criminals, or doing something wrong because we have concerns about privacy, and oppression. Dehhhhhhhhhhhh !
If they want to install such a system of governance, they should say so at election time. Are you aware that the idea that “if you are doing nothing wrong you have nothing to hide” is often attributed to Joseph Goebbels.
http://falkvinge.net/2012/07/19/debunking-the-dangerous-nothing-to-hide-nothing-to-fear/
Sounds like a brain washing response if we do not believe in right to privacy then we admit constitution does not matter. What does? Why we spread democracy to other countries? Colonialism by default?
The things that are being targeted is something that one shouldn’t have to hide.
Perhaps most people really don’t have anything to hide, I’m just a regular guy who lives a regular life.
What if you somehow uncovered some horrible secret that you think people should know about – then you would suddenly care *a lot* about surveillance and censorship. Any journalist with some really substantial information, not just gossip BS, they are a target of the NSA, they don’t want anybody to find out their secrets.
No, maybe the average regular person really doesn’t have anything to hide.
But what if you’re part of an activist or protest group, you’re a homosexual, you’re a member of a fringe politics group.
Then, you might have a lot to hide.
The government is working to extinguish protesters and activists, eliminate those who challenge the status quo, and prevent people from having an opposition to the state.
.
The end result is self-censorship and fear.
If you know you’re being watched, you won’t be very willing to read some article that criticizes the government, and one would be very afraid to even publish something like that.
If you’re a journalist or some regular person who discovers some alarming government abuse like torture or prison camps, you would be terrified that you even have that information, let alone actually tell anybody else.
If surveillance is everywhere, a protest or activist group would have to operate in complete secrecy – or not gather at all.
And openly being a member of a fringe demographic like homosexuals or jews might become very dangerous.
Actually, they are watching you masturbate. The Guardian’s piece on all the webcam images they captured mentioned they were having trouble keeping all the naked pictures away from their staff…
So what you’re really saying is if you’re not doing anything wrong you have no right to privacy.
Blake,
It is what the government is doing with your info that you do not know about. Do a search on “Silent Weapons for Quiet Wars”
You can manipulate and even predict an outcome when you are able to tap into mass amounts of data.
You make a good point, Blake, but then I don’t have a dog in this fight. I simply stay home, mind my own business, be kind and loving to people as much as possible and I do my most important work — clearing my own mind of past battles. if that became a terrorist act — sanity — then getting “fired” off this planet would be the best thing that had ever happened to me. The battle of good against evil can only be permanently resolved in the mind.
When you speak of implanting malware a couple of questions come to mind. What would prevent commercial software such as an anti-virus program from detecting and eliminating this malware or prevent open source development of detection and eradication tools?
The reason that I’m asking is that I believe detection tools are a great means of raising public awareness. When someone sees the report of an attempted intrusion on their own computer they have a more personal connection to the collection of data. Particularly if an origin or purpose is assigned to the intrusion. (Look at Diane Feinstein to see how that personal connection motivates one)
I believe the problem in devicing a program capable of detecting the malware (and *specifically* this one) would be treated as treason. And probably with a drone hit or rendition.
Like the rest of the I.T. industry, they are generously paid to implement backdoors and shut their mouth.
The Microsoft VIA (Virus Information Alliance) allowed the NSA to make great progress abroad in this area.
More good news from our beloved NSA. You are making us feel so secure and safe with all your violation.
coool, more powerpoints from 2005 telling us what we already knew
You were obviously bored by your training sessions in 2005, and I admit the NSA does not create the most scintillating slides. But if you review the documents, you will see they are from five to seven years later, and highlight distinct improvements in the NSA’s capabilities. So no, you don’t know everything. But the fact you think you do is why you’ve been given the menial task of pasting propaganda posts.
I wonder how Dennis Rodman would perform as the next President. He has recently learnt quite a few tricks that can be useful to maintain status quo.
I still like the USA, it is a good country overall.
I may days at NSA, this capability was nonexistent. But Hayden hired web warriors by the hundreds to dominate the web and exploit in in every way. My Snowden has exposed the rotten fruits of their evil labors.
F the nsa
If one lives in the United States, many positive actions have been taken or are being formulated to curtail NSA spying. Perhaps it is necessary and appropriate to mention some of these now. Here are a few links.
http://dprogram.net/2013/12/01/turning-them-off-the-plan-to-beat-nsa-spying-at-the-state-and-local-levels/
http://offnow.org/
http://tenthamendmentcenter.com/
http://www.activistpost.com/2014/02/first-in-nation-arizona-senate.html#more
http://dprogram.net/2014/01/22/tennessee-introduces-bill-to-take-on-nsa-encryption-breaking-facility-at-oak-ridge/
http://www.activistpost.com/2014/01/mississippi-is-tenth-state-to-consider.html
http://www.activistpost.com/2014/03/new-hampshire-house-passes-bill-to-ban.html#more
http://www.activistpost.com/2014/03/oakland-forced-to-dial-back-full.html#more
http://www.youtube.com/watch?v=oGxzK5usAo8#t=159 (Rand Paul Sues President Obama Over NSA Spying)
? Maybe we should consider a class action lawsuit against Microsoft and Apple for allowing mass violations of privacy rights inherent in their Operating System Designs?
Old but Gold: https://portside.org/2013-06-12/86-civil-liberties-groups-and-internet-companies-demand-end-nsa-spying
My point is that much good has already come from the efforts of Mr. Snowden and his chosen group of journalists. Don’t be faint of heart. Fight for your Constitutional Rights while you still have them. Write letters to your elected State Congressional Representatives and tell them what you think about being spied upon by the Federal Government. Suggest that they look into 10th Amendment actions. Get the ball rolling. This matter crosses party lines.
Keep the faith.
Ok, but how many of those actions are aiming to limit or stop attacking non-US citizens? Like Hyppönen said on his TED-speech, 95% of world’s population are “foreigners”, like US gov likes to call us.
Keep the faith Foreigner.
As the citizens of the USA topple the NSA, it will set off a chain reaction in which all of their counterpart agencies in other Nations will come under global scrutiny and they might just topple with them bringing their International Bank of Settlements masters along.
I see the plastic surgeons are now in line for the same shit the NSA’s been catching…….
1984. It comes through the internet via the web cam, not the tele screen!
This is the most important story based on the Snowden documents so far. This program may only be in its infancy, but the developments it describes have the potential to fundamentally change the nature of our society.
One interesting side note is the comparative lack of coverage, so far, of this story in the mainstream media. While factors such as standing DA-notices in the UK, and vested interests in the US may partially explain this, I believe the underlying dynamic illustrates a blind spot in the media. They really have no metric to determine the social impact of a story. Other more trivial stories, such as the bugging of Angela Merkel’s phone, received wider attention. If a story features a celebrity, or has a human interest angle, the press in its mindless way will fixate on those events. But an abstract description of a program like this one doesn’t have a hook to grab the presses’ attention. So far, this story has featured in information technology media, but much less so in the wider world.
But the story is very significant. Most other NSA programs in general can be summarized as the collection, storage and analysis of communications data. The scope and the breadth of many of these programs has been surprising, but it remains essentially a passive activity. This new program has the potential to be much more wide reaching. Taking control of people’s computers on a massive scale, confers the power to filter what information they receive; in other words, it will shape their subjective reality. And it also confers the power to control what they communicate to the outside world, which in turn determines how others perceive them.
The implications go far beyond mere concerns about invasion of privacy. Those who control the programs which control our computers and cell phones, can determinative what information we receive and limit what we can communicate to others. The individual will lose much of their free agency, becoming the pawns of those who operate this system.
This story foreshadows a very troubling future.
Agreed. This is the most Orwellian aspect of the surveillance state we’ve seen so far. With the logical evolution of this technology, the NSA will eventually have the capability (whether or not they use it) to keep a file on every person owning a cell phone and/or a computer, that contains an audio track of all digital activity, nearly everything we say verbally (recorded by microphones), and a good deal of video footage (recorded by webcams and phone cameras). Talk about big brother…
“Skillz”? How old are these people?
Other nations may have honed their skillz, but the US still pwns them. Global dominance is the ultimate online fantasy game.
Thanks Glenn for all you do and who you are – I feel so reassured that “my” government is looking out for me (fifteen years an ex-pat, and no reason to ever go back)
7 months ago, no one ever heard of Edward Snowden. Today he is a celebrated hero. I appreciate what he has done for the world in bringing what is wrong with our government to light.
Had he not the courage to come forward, we would still never know. No one else is talking.
Critical sentence missing:
“You only need to worry if you or your organisation run Microsoft products, particularly newer ones.”
Humbug …iToyz and the MacOS are no more secure
This article must be true, because it’s on the Internet…
… And, yet you read it and posted your comments so that others may read your comments to be true.
I think facebook should be canceled, I think it has caused lots problems for people in many ways,honest and dishonest, I think it needs be deleted
I think Facebook is used and supported by the US gvmt. One company cannot grow such big and fast without the support of money and the US gvmt and NSA need the “social profiles and info” for their spies and agents to better control..
Information = power
and now Facebook has a lot of information in it i like the silly statement that a website mimicking Facebook was
used.. but I think Facebook is aready used by the gvmt, no need to
mimick one
i like the silly statement that a website mimicking Facebook was
used.. but I think Facebook is aready used by the gvmt, no need to
mimick one 
Please shed some light on Facebook and their evil
When this business with the NSA leak first started. I thought well, this guy Edward Snowden is just a trader and commited an act of treason against the people of the United States. Now after listening to all the feds spin and thinking about what his motives might be, its beginning to look more like Edward Snowden is a patriot that saw what our government was doing and new that it was wrong, very wrong, so tyrannical in fact that as a proudly free person and citizen of the United States he new that he must do something to try to stop it. He has placed himself in great jeopardy for the benefit of his fellow citizens at no profit to himself. There is little more he can do to stop the tyranny that our government has undertaken. I guess the rest of the story is up to us.
setagl
“… treason against the people of the United States …” No man it’s not only against the people of the USA it’s against mankind as a whole!! I know you think you are from the land of the free but you just a part of mankind with no special rights over others.
Well, it’s about time!
My partner and I were writing this book already about Microsoft, Windows 8 and how to install Linux when the Snowden revelations were revealed– lots of pieces fit together regarding backdoors, bloated browsers, viruses….. we give the book away for free… http://freeyourselffrommicrosoftandthensa.org/
Thank you for posting this link. Very enlightening background information contained in your book. Well worth the visit to your site.
If you want to escape the senseless NSA spying, just step back a few years in time and remember how we used to live, when living was worthwhile. This is what I plan to do myself. Get off of the internet, unless it is just for work or reading news/weather. Need to research something, go to the public or university library. Send a letter in the mail instead of email, remember how thrilled you were to recieve one from someone? Give the Post Office something to do other than delivering junk mail. Supposedly no body has time to write, but as it turns out, you have nothing but time. You choose to use it the way you want to. Use land line phones (no radio emissions) when discussing private issues, only use cell phones for emergencies and 911 calls. In other words, drop off of the radar from those with prying eyes. Would you tolerate any other types of criminal activities in your life, without taking countermeasures??? Drop out of all social media, who gives a hoot anyway, I haven’t heard of any worthwhile relationships ever develop on the internet, and who really needs to hear real time what everyone else in the world is doing anyway (who could possibly care). If Jesus or Buddha were on social media, would they have had the same effect as speaking in person?? Drop off the radar, that’s my advice, even if NSA makes changes, how could you ever verify these? These people, along with the CIA and other agencies lie for a living, so get used to it, they will always be spying on you. That’s how and why they fit in so well with the politicians, whom they serve so well. Stop complaining and take personal responsibility for your own privacy, deny them access whenever and wherever. Use cash, stop using credit cards. Make no mistake, we’re at war with the organizations under discussion and their lackey organizations and corporations. They have no morals or ethics, only you do. The government will not save your hide, in fact it the last thing they would want to do. You are responsible for your own privacy, make it your priority number one. It’ll take work but one by one, we can drop off the public grid and return to normal society once again. Just some ideas from a simple person. Take responsibility. No one else but you can.
I agree with you mate
I thought the internet was created by the military. Why the surprise that they look. Grow up and as Larry says go out and live life and get off the damn computer.
The internet was created by civilians at civilian institutions. Some of the funding came from the military (through DARPA), but the military never owned or controlled the internet. Until now.
Yes, what Saquatch said.
Where Wizards Stay Up Late: The Origins Of The Internet
That’s a great idea for someone that never needs health care, never takes an airline flight, doesn’t have to work in a modern workplace and has no need to stay in close touch with friends or family.
If you think the internet is the only way to communicate you’re face is too close to your phone screen to realise…..it’s a damn phone.
Health care, organised over the phone. Airline flight is easier to organise over the net but there are other ways. Workplace you don’t have to worry about because usually the company you work for owns the workstations and you’d be pretty dumb to store personal information there.
I checked my laptop for being monitored. Sure enough, NSA.gov is there. I am a single lady and never even had a traffic ticket. I resent it a great deal and take it very personal.
One problem with your plan: the FBI still opens mail, scans it, and reseals it…if you’re on their list that is.
I tried to send a letter to President Obama by sending it to 15 foreign embassies in Washington DC. I only ever heard back from one embassy: Canada. My letter to Pope Francis, along with my letter to the Dalai Lama, were never responded to either. I also sent a letter to the Mexican Consulate in San Francisco out of concern for a young man who was supposed to meet me July 1st to crew for me but he never showed up and disappeared online. I never heard back from them, despite asking for a reply of some kind on the results of their search for him.
I don’t know what substance there is to the notion that the FBI/NSA or whomever is censoring my mail, but given the activities of the NSA with the internet, I wouldn’t be the least bit surprised.
Also, the FBI monitors all Library computers.
As for me, I’m going to HAM and will try to create a VPN Mesh Network that would allow digital open communications between users on the network with interconnections made through HAM. Since the system uses HAM, it falls under HAM laws, which require open communications without encryption, and also that conversations be personal, not for profit-making use. The system would run in parallel with the internet, but would be completely decentralized. Of course anyone could listen, but that’s the point – we need a more open and honest society, not one in which we feel it is okay or necessary to hide what we say from each other. Remember the days of the Party Line?
“Either you are with us, or you are with the terrorists.”
I guess he meant that there are 300 million terrorists hiding under beds in the USA.
With all the gadgetry and spy tools available to different government entities they still can’t tell us where the Malaysian plane is? Couldn’t they all use the satellites and gadgetry to find one 777 plane?!
Ahahahah that’s a good point Omom
The public-facing names of the malware are reportedly “Facebook” and “Twitter” and “Gmail”. Sign up for them today!
The next thing the NSA will probably do is offer fraudulent encryption services if they really do intend to “own the net”.
Oh, that’s already happened. Read up about the NSA connection to RSA, the body setting global encryption standards. They compromised encryption used worldwide and got paid by the NSA to do it.
And since they are already working with manufacturers of computer hardware it seems probable that they could implant something that would decode encryption.
Yeh, the article already said that encryption is not an obstacle for what they have.
Now who seriously believes the “incompetencies” of the spy agencies?
The USA is run by a bunch of dirty bastards, inc. NSA/PRISM/CIA/FBI/SS and the White House crew, inc. Pres. O’bomb-a
Does this site send metadata to third party sites? If so, what does that include and what happens to it?
This site includes Google Analytics and Mixpanel as mentioned in the privacy policy https://firstlook.org/theintercept/privacy-policy/
Yup, and except for Amazon Web Services (hosting, etc. provider) and Vimeo (video hosting), those are the only scripts running on this page (at least at the moment).
If you are truly concerned about these matters, you should probably learn to monitor (and control) the scripts that sites all over the ‘net routinely run in your browser.
For a start, grab Firefox and visit this site:
http://noscript.net/
https://www.ghostery.com/
“Ghostery” a downloadable tracker plug in (and blocker of trackers, “it says”) for browsers (e.g. Safari, Firefox, et al) gives a report listing “Conviva” (an advertising tracker) and “Google Analytics” and “Mixpanel” (both categorized as analytical trackers), sending cookies when on links to “The Intercept” Website. The cookies are supposedly blocked by the “Ghostery” plug-in when the blocking option is active (can be toggled on/off for any particular tracker[s]).
According to an [interview][1] with Intel Corporation representative Frank Kuypers at CeBIT in Germany, Intel is adding a new capability to future processors allowing certain software to remain undetectable as well as making its removal disable features of the CPU. Combine this capability with the NSA’s global malware initiatives and you have the perfect storm.
[1]: https://plus.google.com/+GuidoStepken/posts/bD2VHB4LcEU
Interesting discussion within the comment section at the link. I know which microprocessor I will choose with my next purchase and it will not be Intel.
I am so sick of the government pissing on the constitution and violating my rights. F*** You Uncle Sam I hope someone blows up the NSA like they did to the CIA in homeland.
Hail to the United Secret Police State of America!!! Seig Heil! Seig Heil!
Try to breathe ….
Sieg Heil! (Not Seig Heil: watch the spelling. Must be correct!)
Hasta la Victoria Siempre motherfucker!
Why is this news to anyone? It is not a great leap to assume the NSA would be doing this. Further, it seems to me that Snowden as already made his point. Why is it necessary to keep rel;easing information? He is just on a vendetta, short and simple.
“Move along folks, nothing to see here.”
Because the world, and especially the tech community, need to know the data released today. So people can do work-arounds — where they cannot secure meaningful reform.
Also, Snowden has nothing to do with what documents are published. Those are chosen by the journalists from the trove Snowden gave them eight months ago.
Gradual release of the documents is extremely smart of them to do. What Mona said is correct. What she didn’t say is that if they were released en mass 8 mo ago then everyone (at least the sheep) would have forgotten about them by now. Release over an extended period of time keeps the issue in the public eye for as long as they have material to release. This is EXACTLY what is needed to effect change (if there is any chance of it). It allows the public and the IT community to digest the gravity of it as each peice is released. Additionally it is the only responsible way to release it.
Plus, as an added bonus, the drip, drip, drip of daily revelations, which could go on for years, is driving the NSA and Obama Admin Police State crazy. I’m loving it!
It’s great to have this outlet for actual evidence of NSA hacking but while allot of what has been revealed is very news worthy i’m worried that the tech community need more “technical” information. There needs to be software for example to catch these attacks so that they can be proven and approached in the courts on an individual basis as to their legality. It is well known that there is at least a 6 year gap for legislation to catch up where technology is concerned so if there are supporting technical documents that are related to these even though it might be the same “story” do they stand a chance of being released.
It is certainly possible to develop software to be made available that will be able to prove these attacks and query them as they happen and log breaches. This is what needs to happen, it can then be proven to be malicious and without due process (and all the other things: waist of money etc.)
Using one clock cycle of CPU doesn’t go unnoticed in a computer. It is impossible not to leave a trace, we need help to catch them at it and challenge them. I need every ounce of CPU I have to do what I do for a living, if my hard drive is spinning it is because I tell it to. It is not just privacy it is the property aspect of law which we also ought to peruse.
I always wondered what kind of evil Ba$tard would sit and spend the time to create viruses to attack computers. I surmised it was to stop people from stealing Movies and such but the answer was right in front of me the whole time and I think I already knew it. Its the same people that create viruses that attack the human body. Our Evil Leaders!
Exactly Phil, bingo!
I’m so glad to see so many aware americans here, what will be the date of the first american CIVIL WAR ?
I’m reserving my flight to N.Y. that day.
Does anyone know if NSA buys metadata from facebook, google or third party sites?
Why pay when you can steal?
Does it cost much? Seems pretty convienent, and it may not be illegal. In any case I’d lime to know. What metadata if any is collected by this site? Who or what is mxpanel.com?
Buy?! Why would they need to buy them?
Maybe compensate for any trouble caused.
The classified program named “PRISM” began in 2007 and has signed on Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, and Apple. The recent NSA revelations have laid it all out: The NSA is watching us online. Its overreaching surveillance is creating a climate of fear, chills free speech, and violates our basic human rights — and it operates without any meaningful oversight.
Americans Right to Privacy has solutions and I am anxious to share them with you. We offer secure, encrypted email, a Virtual Private Network (VPN) which secures your computer’s internet connection, to guarantee that all of the data you’re sending and receiving is encrypted and secured from prying eyes. Switzerland, a country known for its strict data privacy laws, has no back door access to encryption for any government agency, not even Switzerland itself.
http://www.americansrighttoprivacy.com
you need to read more. they can inject the encryption, in fact as long as your using wireless they can catch packtes, encase them and send them back altered which is how they upload spyware and malware. in this case it doesn’t matter what vpn you have…they can still see what your doing
Dear ‘United’ States of America (and complicit lackeys):
“Because we can” is not a moral argument. In fact it is indicative of mental problems.
Keeping my fingers crossed that some young, still idealistic NSA operative will have to read this: With all this capacity to attack and control anybody–what happened to attacks on child porn servers, Mexican cartel computers, tax evaders putting their stash into Swiss banks, mony launderers.. these all should be easy to spot and own. Maybe it’s too secret to let on and one fine day, all these above creeps will get rounded up at once.
Or one fine day we’ll find out that above creeps own the NSA and keep all it’s employees duped into thinking they’re serving God and Country, not Sinaloa/ Wells Fargo/human traffickers/ arms merchants?
my best guess is that anybody who publically advocates an end to Fracking will get their computer taken over. Somebody reading this tell me I’m wrong.
Only thing is, this is the spin needed to make everything they are doing alright by some…e.g to have the potential to solve these particular problems in society
Yea, infact! I would also know where can I find those juicy snuff-porn videos recordered with Iraqis children and women lock down in Abu Grahib.
There sure are a lot of people leaving comments that really have no idea what they are talking about. How many of you work in the Security sector? Programmers? Hmmm… not many i see. Perhaps try learning something about how the internet works before leaving mindless comments to confuse other people trying to learn something.
All this post is, is a re-hash of what Snowden has been leaking for months. Like it or not, this is actually happening. It’s not a fairy tale, it is REALITY.
I strongly urge you comment trolls to get on the right side of the fence. You are not helping your nation and fellow americans by spreading disinformation on website comment sections.
All you’re doing is harping on the commenters. Do you actually want to comment on the contents of the article?
Not the comment of a programmer. He did comment on the article, for those he is addressing they know who they are..
the trolls are paid by the NSA to spread more disinfo just ignore them.
As long as they don’t look at MY LIBRARY CARD, like that Evil George Bush was gonna? They can do whatever they want.
Signed: The Left.
SSL is end to end encryption. When you communicate with an HTTPS website, your HTTP request (and also a randomly generated symmetric encryption key, generated at the time the request was made) is encrypted at your computer with the destination server’s public key, and becomes an HTTPS request. The HTTPS data is routed through the ISP to the destination server, which then decrypts the HTTPS data with their private key. Their server finds the file (usually an HTML file, or a resource like a PNG image) specified in the now decrypted HTTP request, and uses the supplied symmetric key (which was also encrypted along with the HTTP request) to encrypt (via AES, or 3DES) the file in question. The encrypted file (HTTPS reply) is then sent back to your browser (routed through the ISP) and your browser then uses its copy of the symmetric key to decrypt the data (webpage, resource file, etc). The government does not have access to the private key of the server you sent the HTTPS request to, and therefore can not decrypt your HTTPS request. Further more, because the HTTPS request cannot be decrypted by the government, the government also doesn’t have access to the symmetric key and therefore cannot decrypt the HTTPS reply. HTTPS is basically hardened against all kinds of attacks, so even if man in the middle was performed by the government compromising the ISP and they stole all the data passing through the ISP, they still wouldn’t be able to recover the HTTPS stuff. To crack any kind of key with the bitlength used by most modern encryption standards, it would be impossible to brute force it, even with a supercomputer. It would require literally a quantum computer to accomplish. And those are just barely in the experimental phase, able to do only the most basic arithmetic like 2+3=5. Though they have potential to be trillions of times faster than the best supercomputers we have now, they currently don’t even live up to the capabilities of the old vacuum-tube computers like the Univac, Eniac, and Edsac, all of which are so huge as to fill up entire rooms (and by the way, the current quantum computers are just as big, because even though their main functioning parts are atoms, the equipment required to support their operation is huge, even with modern technology). It will be decades before the NSA (or any other agency with interest in quantum computing) will be able to get them even up to the ability of current silicon-based home computers, even with the best scientists in the world working on these projects. It will be well over a century before there are quantum computers that surpass modern supercomputers to a sufficient degree as to make it possible to brute force any long bitlength key within the time period of a human life-span. And until that has been achieved, the NSA (regardless of their vain bragging) will NOT be able to crack HTTPS, SSL, RSA, AES, or any other encryption. Now any of those that rely on human typed passwords will be weakened by the human-factor (people don’t like long complicated passwords, because they are hard to remember, even though they are more secure), but those such as automatically generated RSA keys are VERY immune to brute forcing with anything short of a quantum computer.
What you should be saying ( and maybe it’s buried in there somwhere ) is that the mathematical basis for encryption is still valid ( despite much misinformation trying to discourage its use ) .
The fact that the spies are trying to infect computers and obtain encryption keys or data before encyption tells you how good the actual encryption actually is…
So what? Someone with that much power can just get a SSL certificate for their own server from one of the browser-builtin cert agencies, and none of the major browsers would be able to detect it (the last-known cert is not stored, wouldn’t be possible to store in private mode anyway, and then there’s the problem of the initial connect which could already be hijacked), so unless the user goes and compares cert fingerprints (with what?) on his own, he would’t even notice.
If they don’t have facebook’s private key anyway.
Theoretically, no. But they could force a certificate authority to issue them a certificate as if they were, say, facebook.com. Voila, you go to https://facebook.com, and you might be in some other server, even though there are no security warnings from the browser. For that matter, right now we could be exchanging comments in a server that is not firstlook.org, despite the connection being ostensibly secure. And there would be no way to know if it’s a man-in-the-middle as opposed to a DNS attack. (FWIW, here’s the firstlook.org IP I get: 4.53.16.143.)
More importantly, here’s the cert’s digital signature reported by the browser for firstlook.org: ?c8 9e bf 71 4d eb ba 8e 3e 15 d8 99 27 99 79 86 2a 75 c6 f1
As long as they don’t go looking at MY LIBRARY CARD, like that Evil George Bush was gonna, I don’t care what they do.
Signed: THE LEFT.
There is only one way for the United States to save face on this, and that is to completely defund the NSA and all of its activities and bring the department under criminal investigation.
In this way, the illegal activities of a rogue agency can be separated from the nation it is supposed to serve. But this would be a committment to the highest level of reform of the US Government, and would require a gutting of the executive branch of government. Doing so would save Congress, for now.
Of course, we all know that this will never happen. I firmly believe that the only real solution available to the American people, is a complete replacement of elected federal government. By creating a new political party and quickly putting a presidential candidate and candidates for all available offices of Congress, and by presenting the party openly and honestly to the American people; a new power can emerge in Washington which promises to sweep away the corruption. If fully one third of both the house and Senate can be replaced, along with the President, by this third party; the federal government can be handed back to the American people.
Only then can action be taken to undermine the criminal actions of the federal government, including the NSA. And by running on a platform of opening government and ending America’s illegitimate nuclear reign; we can not only save America for Americans, but for the world as well, and with our infrastructure, restore America to a global power, leading this time by example, rather than the might of the nation’s nuclear muscle.
I don’t know how to organize people, but have been running an internet show on Youtube under the username zapocalypsediaries. This is a fictional show, but can be a means of organizing; as such means are not made readily available to us here in the United States. I am hoping to inspire or directly organize people to form this party. I am willing to act as a consultant, but will only take up nomination if asked. I do believe I have what it takes to make for a good president, as I care nothing for money and everything for people.
I don’t know what else I can contribute to this problem. It is an unprecendented problem for the most part. I have been asking myself what it must have been like for Germans during the rise of Hitler. Given that the very same techniques were used in Germany then as are being used now (namely Propaganda), I have found that attempting to organize Americans is rather fruitless; thus the show, its content, and its aim to reprogram people, to undo the brainwashing that a lifetime of television has inflicted upon us.
Oh, and a question – is it just me, or does the NSA seem more like internet trolls than actors in national security?
What makes you think the NSA is rogue? It’s doing exactly what its masters have ordered. Relax. Resistance is futile, but please complain all you like.
when spooks spy on the legislators you know they must have got control over some thereof,
just common sense and Hoover……..
Yes, they seem more like Internet trolls.
Agree – and not all American’s are influenced by the propaganda. VIVA LA REVOLUTION!
Does no one see the legal loop-hole here? A person can now do whatever they want, just blame the NSA since they are ‘inserting’ things into our devices: “I didn’t write/do/say that, the NSA clandestinely wrote/did/said that posing as me!” Gives new meaning to – ‘The Devil Made Me Do It’. Make sure you keep a few hard copies of this article. Send one to yourself and one to your lawyer via certified mail. Instruct your lawyer not to open it until the need should arise to present it in a court as evidence against the NSA.
Americans Right to Privacy has solutions and I am anxious to share them with you. We offer secure, encrypted email, a Virtual Private Network (VPN) which secures your computer’s internet connection, to guarantee that all of the data you’re sending and receiving is encrypted and secured from prying eyes. Also a “Swiss Bank Account for your Data” Digital Safe! Switzerland, a country known for its strict data privacy laws, has no back door access to encryption for any government agency, not even Switzerland itself
We offer a professional global email service solution for both personal and business use. PrivacyAbroad email service is free of advertising, SPAM and provides private communication with your emails saved and backed up in Switzerland, renowned for its strong data privacy protection laws. Email comes with 1 GB of expandable storage space.
Your search for online privacy is over…
http://www.americansrighttoprivacy.com
*… Americans Right to Privacy has solutions and I am anxious to share them with you…*
You are not ANXIOUS but greedy to make MORE $£€ with it no? Every opportunity is good, isn’t it?
You do not seem to have understood the core of the article (I am 100% sure you did not read it because your only concern is money), you came here to advertise your company… which is SWISS, country where the banks like your company act as gangsters to enable rich people avoid paying taxes. Shame on you ! boooooh
Be careful btw NSA is watching you too
Eddie Bates
@eddiebates23
Proud American & even prouder Texan! Has-Been golfer who can still break 80 at any time! Sober since Oct2008 Loving life and @ColleenAstedt loves Me!!!
*… Sober since Oct2008…* which means that before Oct2008 you were an alcoholic like a certain G.W Bush, Texan citizen too Since then he is a *christian-reborn or reborn-christian*
Since then he is a *christian-reborn or reborn-christian*
I like very much the purpose statement of your company :
Effectively serve our resellers, customers and employees, PrivacyAbroad is committed to:
– Bringing glory to God in all that we do by operating in a manner consistent with Biblical principles.
– Serving our employees, resellers and customers through encouragement, integrity, and value based policies.
Come on! are you joking bending yourself in front of a supposed god ?
Too late, it’s already complete.
Can you believe this crap?
Barack Obama is going to let Mike fuckin’ Rogers head the NSA? And DiFi is huffing about spying (who’s due to retire)? Fuck me but Dick Cheney could get a few tips from this latest authoritarian.
http://www.emptywheel.net/2014/03/12/in-nomination-hearing-dirnsa-nominee-mike-rogers-continues-james-clapper-and-keith-alexanders-obfuscation-about-back-door-searches/
These fucktards lie without blinking. Likes Charles Manson. No, wait, my bad- at least Charley didn’t lie, he admitted it proudly. Psychopaths are running the asylum. Fuck me runnin’.
These fucktards lie without blinking.
Do nictating membranes count? :-p
Had to look that one up! (nictitating membrane). Very apt, sis.
I think you might be mixing up your “Mike Rogers’”? This is Vice Admiral Mike Rogers they are referring to (http://www.politico.com/story/2014/03/mike-s-rogers-nsa-nominee-surveillance-104537.html) and not congressman Mike Rogers.
I know who I’m talking about. Thanks for your concern.
LOL, sure you did.
Change, change, change… The SAME, The SAME, WORSE!
Psychopaths are running the asylum.
I don’t think you’ll be peekin’ through that fence. ;-}
p.s. I spelled “nictitating” wrong. Glad you found it, even with the headfake. Cool word. Right up there with “coprolalia”, another infliction associated with (some) members of this, ahem, class of people.
the blood is on our hands now
The NSA is your friend.
I loves you
and is there to protect your freedom.
Do not be afraid.
It is all good.
Ahahahah Mollie, what’s that, evangelist church preaching or they gave you double sugar coffee this morning ? NSA is the evil. NSA is the end of the human being. Prequel to terminator3
Where have I heart this before…
“Following the destruction of its major assets, Cyberdyne was ruined financially but some of its research and plans survived. The United States Air Force purchased the company and started in-house development of the projects in its Cyber Research Systems Division (CRS). After years of work, CRS had nearly completed Skynet, a software system designed to make real-time strategic decisions as well as protect their computer systems from cyber attacks. Due to the massive computing needs and to protect it from direct attack, Skynet utilized a large network of computers that would be nearly impossible to deactivate completely. Unknown to CRS, Skynet began to spread beyond its original computing base through the Internet and various other digital media.
Prior to Judgment Day, Skynet had penetrated nearly every networked machine in the world, causing malfunctions in everything from barcode scanners to nuclear launch systems. This was originally believed to be the effects of a new virus, and increasing pressure was placed on the CRS to purge the corrupted systems. The CRS attempted to eliminate it from the U.S. defense mainframes by tasking Skynet with removing the infection, effectively telling the program to destroy itself. Skynet took control of the various machines and robots in the CRS facility and used them to kill the personnel and secure the building. John Connor attempted to attack Skynet’s computer core, hoping to stop it before it proceeded to its next attack, only to find he could not. Skynet was pure software and on too many systems to be attacked. Shortly afterward, Skynet began a nuclear bombardment of the human race with the launch systems it had infected. Judgment Day occurred despite Connor’s efforts.”
– http://en.wikipedia.org/wiki/Skynet_(Terminator)?
Eventually people will become so disgusted that they will use infect other’s computers and use them as bots that randomly send messages with dangerous words in them and pictures of random places, this will keep the pathetic drones busy chasing ghosts.
there is an APP for that……..
ahahahahaha share the name of the Appp !
I’d like to get some fun.
slate.com ran an article
scaremail
benjamin grosser
search terms…..
Peeping NSA Toms are even in your toilet! Don’t forget to flush!
ahahahahahahah
Hi
I get it… and it is dangerous… but I have to add some other element.
Our power grid has been infiltrated. Can this whole NSA thing stop an attack on our infrastructure? Can something positive come out of this?
not, in my opinion.
only for the State………
Everywhere is a public place now. Peeping NSA Toms are even in your toilet
Everywhere is a public place now. Peeping NSA Toms are even in your toilet. Actually, that’s right where they belong, FLUSH!
VERY dishonest and misleading reporting (all of it, not just this latest version)
They DO NOT only have capacity to REMOVE data, but PLANT it as well
You NEVER see that discussed. Think about where that goes.
Want to cause a stock market crash? Plant phoney sell orders
Which bit is dishonest and what do you find misleading?
It would be a VERY dangerous to plant something i.e a photo as this would be evidence of a system breach. It is not necessary to plant phony sell orders to cause market crash the FED can taper etc to cause these which would be easier. It is important to note that things are planted that allow remote control of target computer including possibility to plant naturally.
It can only be a criminal offense to hack a computer without a warrant..
They did say that the NSA is “planting” malware and scaling that up. Maybe planting of data is a future topic. Do you know something about the NSA planting data, or is that theoretical?
You might have proposed a mechanism to quick-transition from the exploitive capital market. Let’s plan a better economy, shall we? RDWolff.com
As for planting false data for blackmail: You didn’t suggest it but your premise leads there. Everyone has a human right to their personal and private information/knowledge. When that is violated, most people can be “owned”; there is no need to “frame” them. By the way, these journalists are not doing this, but maybe that should be on the agenda. I don’t want to see John Brennan and his mistress’ kinky photos, but it is well past time to dump evidence of his war crimes on Wikileaks (or even YouTube if convenient).
This article links to this New York Times article which covers it (http://www.nytimes.com/2014/01/15/us/nsa-effort-pries-open-computers-not-connected-to-internet.html?_r=2)
So spare us your whining.
The US government has turned into a criminal organisation.
The appropriate response would be a total UN enforced embargo – isolating the USA form the rest of the world until they start behaving in a civilized and law abiding manner again and the responsible ones face justice in an international court.
@Horst – Good luck with that. Do you even understand how the UN works other than the fairy-tale visions in your obviously undeveloped mind?
Here is some help:
http://www.heritage.org/research/reports/2010/08/us-funding-of-the-united-nations-reaches-all-time-high
http://en.wikipedia.org/wiki/United_Nations_Security_Council
http://www.un.org/en/peacekeeping/contributors/2014/feb14_1.pdf
Go back to watching cartoons.
I absolutely agree. The USA seems to be trying to stir the pot every which way it can and call all Americans crimminals when their government agencies ,cooperate TPP friends can dictate,bomb and destroy anybody the want without without probable cause or retobution. The next thing you can only guess ‘WORLD WAR 111’1
NO INTERNATIONAL COURT ANYTHING GLOBALIST!
The modern American Nazi,
Khakis, button down or a suit at some agencies, and if a contractor even less causal. Two kids and SUV, exercise class and Starbucks coffee on their way to the office and they are clueless as to the Bill of Rights and what it really means. Known a few, was married to one.
The deployment of mass surveillance programs sickens me and it ought to sicken those people but a GS13 in the DC area makes roughly $125,000 so it will never happen.
The can all BIH
“Don`t use E-Mail, G-Mail, Skype, facebook,twitter,etc. Go back to the old fashion time honored hand written letters, and use notes instead, at least that is what a lot of reporters arenow doing instead of the internet and e-mails, also use word of mouth if you have to due to this sicko NSA and their nefarious cabals,etc,etc,etc”!
This is just a false flag. If you run Windows on your computer, and probably 95% do, then you already have been hacked. Microsoft puts NSA backdoors into every copy of Windows, so this is just a diversion.
I’ve been running a Mac workstation for seven years with an OS that doesn’t have a back door because I refuse to update to their bullshit. Works fine with the added feature of a back door denier (I prolly have 500 dead trojan horses locked up).
What do you mean by a ‘false flag’ btw? I know the term well but am interested on what yer talkin’ bout.
There are always Flag possibilities but this one is not one of them. This is comprehensive evidence of particular techniques used to access systems by NSA/GCHQ et al. Even though a heavy percentage (95%?) what is to stop microsoft addressing it’s backdoors in future OS development for example. This article includes evidence of ‘man in the middle’ etc which doesn’t require the door left open, and there were plainly not thousands of warrants sought for this number of attacks which is one the main things this article points out (to me anyway).
Diversion from what? We need evidence to change policy and this and other docs are providing us with the means to protect ourselves and the evidence needed to debate upon some way to change this activity.
Imagine the over the top existential catastrophic portrayal this issue would receive from the MSM if Bush (or any Republican) were president and this crap was going on.
Since it’s obama (or if it were any democrat) they are downplaying it in order to prevent exposure, embarrassment and political hardship.
There’s really no other way to look at it. The MSM are either epic hypocrites or a wholly owned subsidiary of the democrat party.
so why isn’t fox reporting on it?
Did you not notice that this Intercept article includes several links to the New York Times and Washington Post’s (i.e. the “MSM”) coverage of these exact topics?
Here, let me give them to you:
http://www.nytimes.com/2014/01/15/us/nsa-effort-pries-open-computers-not-connected-to-internet.html?_r=1
http://www.washingtonpost.com/world/national-security/us-spy-agencies-mounted-231-offensive-cyber-operations-in-2011-documents-show/2013/08/30/d090a6ae-119e-11e3-b4cb-fd7ce041d814_story.html
http://www.washingtonpost.com/world/national-security/stuxnet-was-work-of-us-and-israeli-experts-officials-say/2012/06/01/gJQAlnEy6U_story.html
http://www.washingtonpost.com/world/national-security/us-israel-developed-computer-virus-to-slow-iranian-nuclear-efforts-officials-say/2012/06/19/gJQA6xBPoV_story.html
So the second and eight ranked newspapers in terms of circulation (http://en.wikipedia.org/wiki/List_of_newspapers_in_the_United_States_by_circulation), reported on this but are somehow “downplaying it in order to prevent exposure, embarrassment and political hardship.”
It’s not all some big conspiracy, the information is out there.
Of course the hardcore types are here and are all in agreement. But outside of them, I don’t think people are responding to these “bombshells” in quite the way you think they are.
When a troll is right, he’s right. These articles probably get 1% of the readers that the latest Bieber news get. That doesn’t reflect badly on the reporting, though. It reflects badly on (1) the general population’s awareness and intelligence, and (2) mainstream media self-censorship.
But it’s not like folks like me spreading the word to otherwise ignorant people. I’m guessin’ you like ignant folks. Um humm (h/t Slingblade).
There was a time (pre Obama) when I would say that it is important for a just and lawful government like America to know this information to protect the world, but with a President who won’t own up to BenGazi, Libya, IRS Targeting, and politicizing every branch of government that was once neutral, even the surgeon general, and when Congress is looking out only for themselves, and when the Supreme Court helps reword Obama care so they can pass it as constitutional, I ask if this is the America where the rule of law ruled over the whims of man. So, this NSA overreach bothers me now because I can’t assume, as I once did, that the purpose is to defend democracies over totalitarian regimes.
Ha. Exactly how long “before Obama” was that?
Dec. 7, 1941?
And when was the mission to protect the world?
BENGHAZI!!!!
Everybody’s favorite scandal that wasn’t…
Michael, please. Some of this started in the Clinton era. The programs gained momentum under GW Bush. It was the Bush administration who authorized torture of prisoners, invaded Iraq on false pretenses, and set up unconstitutional surveillance of US citizens. Obama’s great failing is that he has not stopped any of this criminality except the outright torture. But I think the intelligence services have gathered enough power to essentially call the shots with regard to their budgets, their spheres of operation, and their choices of techniques. The official US government is a false-front, for the most part. That goes for Republican as well as Democrat, conservative as well as liberal. The controlling power is elsewhere, and the security services are part of that reality.
The people who run and work at the NSA are literally PSYCHOPATHS!! Why is the NSA allowed to exist? The NSA is a threat to the whole world!
My computer froze up upon clicking on the link to this article from Facebook. Coincidence?
take your meds.
Hey Schmuck. You can go back to living in a world full of flowers and butterflies and pink elephants….OK?
Commodore64 is not your friend?
Dear Mr. Greenwald… please forgive me because this is totally OT – but the comment board is blowing up and I’m pinched for time. When you’re reworking the board comments section can you please provide the ability to:
1. Follow/UnFollow: specific Commenters, Conversations
2. Filter/Watch: Conversations I’d like to follow… this is more so I can still follow commenters/conversations when a troll is babbling or the conversation.
3. Receive alerts based on my user preferences and how I tick the boxes of #1 & #2
I know these are first-world problems… I’d do it myself but I haven’t written “code” for over 20 years and a lot has changed. Please don’t respond – just wanted to put this in a suggestion box. Go back to your writing. Thank you.
p.s. Dear NSA – since I know you’re reading this – BTW – I really don’t like a bunch of suits breaking into my house, especially while I’m taking a shower, and watching or raping me. I never sent you an invitation – and I promise you a rose garden. Trust. You people are creepy, freaky, sick, deluded fuckers. Just a heads up. Have a nice day
CORRECTION: – and I NEVER promised you a rose garden.
I’m so pissed about this new revelation even my fingers are spitting!!!!
is there any info on which country is the fifth eye ?
I don’t know what you mean by “which country.” I don’t think there is a specific or ordered 1,2,3,4,5 sequence. Each is an eye is an eye is an eye: Australia, Canada, New Zealand, the United Kingdom and the United States
Do they understand just how angry Americans are becoming?? Ssure they must and with Obama not only not prosecuting perjurer Intel Director James Clapper, HE RETAINS HIM!!?? Could Obama actually be seeking 1st blood on the part of Constitutionalists (Note I did not say Left, Right, Tea Party, Republican, Democrats) to enact serious Executive Orders? I would have thought that crazy talk a year ago, not so much any more.
Last June Sen. Dianne Feinstein called Edward Snowden a traitor, well, well,…don’t feel so good when the spooks are doing it to you Diane does it? But then again, we are just the little people aren’t we?
We know that the NSA will lie about their contract employees,..When the CIA and NSA were confident they had agent Snowden corralled in Hong Kong and arrest was imminent they would have made Joseph Goebbels proud,they released false and partial information; “failed in the military” -
Lie, he had a medical release due to training accident,..failed high school- Lie, he had meningitis and had to complete his studies by GED. They even tried to make him out to be stupid, by the time he got to Russia, he showed them who the brighter one was.
He risked his life or a life behind bars, for what? No money rewards, actually he sacrificed a great wage,..for fame? In exchange for a hellacious price in exile?, I doubt it,..I believe Ed Snowden did it for us, for our Constitutional rights. Agent Snowden turned the political paradigm of Left Right party politics upside down and inside-out. Snowden forced them to show their true colors, We have those like Rep.Ron Paul who understand that Snowden could not just go up the chain of command, he would have been quietly dealt with and I would not be writing this and you would not be reading this. The last thing the NSA or Clapper wants is this ex-contract intelligence agent Snowden’s charges dropped and him testifying before Congress. No matter what the intelligence community spouts, Snowden revealed no field agents, no technologies except those that were used against American citizens while criminally breaking our Constitutional laws.
Patriot Snowden will go down in history with the likes of Patrick Henry. Unfortunately I fear his fate may be the same, and straight out of the lyrics of Secret Agent Man,..
Oh, be careful what you say,
Or you will give yourself away.
Odds are you won’t live to see tomorrow.
Snowden is still alive and free to speak to the world community. He reached 337,000 world citizens in his live-streamed address to SXSW on Monday, March 10. During the past nine months, the US Government – DOJ, NSA, CIA, Obama, Kerry and others – and their UK GCHQ partner and supporters have tried everything in the book, legal and illegal, to silence him. They have failed and they are in shock that they, with all their power, threats, and coercion, didn’t succeed in killing him or jailing him and treating him like they did Chelsea Manning. He is in Russia, currently the safest place for him on earth. He didn’t plan on ending up there but he did. Isn’t fate great?
Superb article. I will have to read it again tomorrow and have a look at the docs too. The best so far along with the online covert agents article and drone SIGINT intelligence one. Thanks Glenn for getting this out so quickly, and making it clear that this is just the Intercept in its early stages, so I look forward to more great reporting like this but more of it, more regularly.
I will assume the NSA/CSS has “infected” this device. When, not if, civil disobedience and worse begin, these facilities will fall. When, not if,is why these agencies are doing this.
Terrorism is a word. The definition depends who is defining it.
It is anathema to America’s constitution and transgresses all humanity. Those (yes you) that commit such acts will say I was only following orders as millions have said before but justice was still served.
and…..? do you think the US is the only nation that has this ability?
What’s your point, idiot?
If you move to Stockholm maybe you will find kinder fascist masters to watch over you.
To me the real terrorist are the leadership and employees of the NSA…they claim what they do is to “keep us safe” by “us” they mean the government
(this will prob get censored like my other comments) That’s why some webpages take so long to load. They are transferring data from your computer to theirs. Wondered why data travels through many different unrelated sites, and social networks before you get your article. Be a good social networker and “like” these companies so they can spy on you. What is a company doing on a social network anyways.
I’ve been using Windows 98 all along, and after reading this I am definitely going to keep using it. And contrary to popular belief, it is very usable in terms of web browsing and video watching today.
How’s that rotary dialing working for you?
Please tell me you are kidding, ahahaha
If you like your health insurance, you can keep your health insurance.
If you like your doctor, you can keep your doctor, period.
If you like your privacy, you can keep your privacy.
If you like your constitution, you can keep your constitution.
Get it?
You seem a bit confused about who was president in 2004.
Then, the health insurance line, right so a lie of omission, “provided it’s exactly the same health plan you have today in Sept. 2009, yes you can keep it.” Is as serious as these abuses?
no need to sound off, true believer. we already know what you think that you think.
I’m a software engineer with 25+ years of experience. I’ve implemented a LOT of networking code. From reading this article, my long-held suspicions appear to be confirmed. The TLA’s (three letter agencies) have successfully exploited the entire spectrum of network protocols, even though they didn’t really have to.
(For example, basically security boils down to “you have to trust someone” – your computer / home router HAS to trust your ISP’s internet gateway, which then provides links to services such as DNS, which HTTPS (TLS/SSL) then rely on. IF this ONE ‘choke-point’ is compromised, you’re owned. The TLA’s didn’t have to own the entire spectrum of infrastructure, but they did anyway.)
Every time I read another of these revelations, it makes me realize that I’ve (complicity) helped create a monster. I’ve become more and more reticent in participating in developing this technology. Having witnessed the evolution of commercial surveillance technology first-hand, and now learning about the even broader & deeper government surveillance technology, I’m seriously considering just getting out of technology entirely.
If my reaction represent the typical user (if somewhat elite from a technical standpoint), this all will deeply hurt the US economy and technical base we we start to leave en-mass. I’ve built big systems that sustain billions of dollars in transactions per year; now I think that this experiment we’re performing in ourselves is just wrong. On so many levels. We’re no better than the Chinese. We spy, torture, pollute our world with abandon… This is not going to end well. Let someone else build the advanced systems of tomorrow. I think I’m going to retire, buy a cabin in the woods somewhere, and let others help destroy the world. I’ve had it.
It’s too bad – we’re on the cusp on world-saving technologies such as plasma jet fusion for power generation. But I honestly don’t think we’re going to make it across the technology bridge to a better future. Not when we squander our wealth on vile technologies described above, allow corporate media to control the ignorant masses with propaganda, and enrich the rich at the expense of the poor.
I had such high hopes for Obama…
(and Yes, I’m very aware that despite this being a HTTPS site, that’s just creates a false sense of security and that my post (and your reading the post) is very very likely to be added to the ‘file’ that the government / corporations keep on each and every individual who has ever touched a ‘connected device’.)
Jay:
Then don’t read this website on a computer that can be linked to you, and don’t use an email that can be linked to you.
Really, this is news?
And just how is that done? There is a trail that can be tracked 20 ways from yesterday
Bill, reread what I wrote.
If the computer and its use can’t be linked to you, then it’s easy enough to hide activities from this kind of spying.
For example, how as long as you don’t use your named email would a computer in an Apple store track you specifically? All the servers connected to that computer see is someone surfing from the Apple store. As long as you don’t provide some name.
You watch, Russia, China, and other countries will build their own internet that will be closed off to all US contracts and users. But the NSA will have more control over internet within borders and less control outside. Not necessarilly a bad thing for THEM since Americans will be force fed propaganda and in the dark about the outside world. Just like when Hitler took power.
No, it does not “have to trust” the ISP gateway. That’s not true at all. (It is true that, in the vast majority of cases, “your” system at home is organized in such a way that it does trust your ISP, but it is perfectly possible to treat that entity as hostile.
You (certainly, with your level of expertise) and potentially every other user on the Internet have the ability to choose which DNS server(s) you use. Nothing forces anyone to use the one(s) provided by an ISP.
This isn’t even remotely close to the truth.
You may have written a lot of networking code, but you need to review the standard protocols of TCP/IP communications and the options for implementing them. You are providing fundamentally inaccurate advice.
You’re not getting what he is saying in the post. It doesn’t matter if the DNS belongs to the ISP or another DNS service. You still have to trust it. Even with VPNs you’re still placing trust on the VPN. If any of these get compromised whether covertly or complicitly you’re screwed.
No, it’s you who don’t understand. One of the things you don’t understand is that you could run your own DNS (or any other) server, and so could your friends, neighbors, trustworthy local business or community organization. And each or all of those can also run VPNs.
Dave G is just plain wrong.
N.B. If DNS is compromised at the level of the authoritative name server for a domain, of course, the altered responses will be propagated through the system. However, exploits like that tend to be discovered fairly quickly.
read and compile source code, build the network infrastructure….you’re just plain wrong.
“…pollute our world with abandon… This is not going to end well. Let someone else build the advanced systems of tomorrow. I think I’m going to retire, buy a cabin in the woods somewhere, and let others help destroy the world. I’ve had it.”
At least one renown biology professor from an R1 university took this route (GuyMcPherson.com). He explains that our triggering of 30 some self-reinforcing climate/environmental loops in recent years will likely cause near-term extinction of humans by ~2030. We are in the midst of the 6th mass extinction now, loosing some 200 species per day.
Forgive my following your “tangent”, but nature does have everything connected. And, please forgive the “heavy rap”. McPherson (and many others) doesn’t think environmental engineering can save Gaia as we know her (or us), but he does propose living it out with peace, dignity, and respect for the biodiversity we will be leaving behind. We can apply the engineering to controlling the fascists of the world. Let’s try to make this worldwide revolution peaceful, but we might keep all potentially effective options on the table. As we review and probably abolish the death penalty, Brennan, Chenny, Clapper, Alexander… Bush… the Kenyan guy… and criminals of their ilk may or may not be amongst the last to go that way (too easy for them, yes). If we keep them, may they completely transform to revile every one of their criminal deeds and every aspect of their former self(ves) that enabled their criminality. May they also wear the shame of their crimes for all to scrutinize forever more. And, may they serve society in some appropriately guided way for the rest of their days.
Today, regaining your online Privacy means going Abroad
http://www.americansrighttoprivacy.com
If the NSA has turned into a ‘monster’ like Frankenstein, let’s say, then it is incumbent upon the scientists that ultimately built the
Frankenstein to unbuild the Frankenstein. Scientists that now feel guilty about their involvement have an obligation to articulate
why they do not support the Frankenstein that is now abbreviated NSA. The American National Security Agency has actually morphed into
something very grotesque to the very scientists that built their capability. In brief, contemporary science and scientists, as well as academic
scientific institutions owe civilization and academia more than the National Security Agency gone rogue, BuckO!
But the monster has intelligence, and no longer needs scientists
Dave G – Thank you for such an honest and thoughtful comment.
The world would be a very different place if everyone realised how unconsciously complicit we are in all sorts of areas of our lives. And then took very real steps to choose differently.
“The man-in-the-middle tactic can be used, for instance, to covertly change the content of a message as it is being sent between two people, without either knowing that any change has been made by a third party. The same technique is sometimes used by criminal hackers to defraud people.”
Isn’t this redundant?
THANK YOU! GREAT ARTICLE!! KEEP IT COMING!
Now, class, yesterday Sen. Feinstein claimed that the CIA/committee spying breached the the Computer Fraud and Abuse Act. You’ll find it in Title 18, US Code, the Federal criminal code, specificially 18 USC § 1030.
http://www.law.cornell.edu/uscode/text/18/1030
If this law sounds familiar, it’s what the US Attorney charged Aaron Swartz with.
http://s3.documentcloud.org/documents/217115/20110719-schwartz.pdf
see also
https://www.eff.org/issues/cfaa
Now, applying the wording of 18 USC 1030 (see Cornell, cited supra) to today’s fact pattern, how many different breaches can you spot?
Discuss.
The counter is spinning so rapidly that I keep losing track and getting all confused.
It’s a good thing for those spooks that they have de facto immunity.
So… the NSA has already gotten the public viewpoint skewed this far??
NO government malware is acceptable. NO EXCEPTIONS!!
Anyone who says differently, including Hypponen, commits treason!
Just a matter of time before non-US countries build their own internet, alienating American users about the truth in the world. They are already taking their business elsewhere. They are building new fiber across the ocean. US tech companies should be mad a heck since it will be hurting their bottom line. NSA can have a spyfest by spying on Americans as I believe is the true intention.
More than that, now that the US has infected computers everywhere indiscriminately with malware, every country in the world can now claim the right to do the same in the US, as a proportional retaliatory response. They constantly talk about the threat of cyberwar. They could very well have started one.
It is this country’s “Law Enforcement” who enable this swill. Every one of them swore an oath to the Constitution before they pinned on that badge. Yet not even ONE of them will arrest these maggots for their treason.
“I VUS CHUST DOINK MEIN CHOB!“
Precisely.
“The agency sought $67.6 million in taxpayer funding for its Owning the Net program last year.”
Isn’t that nice, using taxpayer funding to spy on the taxpayers.
“According to the Snowden files, the technology has been used to seek out terror suspects as well as individuals regarded by the NSA as “extremist.”
Here in the United States the government has defined “extremists” to include conservatives, Christians, Republicans, those who support the US Constitution, those who deny global warming, and military vets. Of course the definition of extremists depends on which political party the head of NSA belongs to…
“The mission, codenamed “Operation Socialist,” was designed to enable GCHQ to monitor mobile phones connected to Belgacom’s network.”
Operation Socialist is an appropriate name since Socialist/Communist states depend on absolute control over the people in order to rule over them. Without privacy there can be no individual freedom.
Great work here, really glad there are people out there like yourself Glenn and the people working hard at The Intercept to bring us this information in the comprehensive that laymen can understand. I have a good picture of what is going on here and see why Ed made the sacrifice he did leaving Hawaii and the cushy job at the NSA. Again I appreciate your hard work.
Thanks.
I’m looking for the people who, just last Friday, confidently proclaimed that we clearly had no more significant stories left and had used up all the good parts of the archive: all because Peter Maass wrote a light but still significant and interesting story about how even the NSA’s own employees recognize the toxic effects of privacy violations when applied to them.
Let me know if you see those individuals.
And, as always, there are a lot more to come.
Russell Tice.
This Peter Maass article among others (Snowdens testimony to the EU etc.) are stories I had not seen until I read thru the comments section here and then searched them out. Where I use google news with sections for both NSA surveillance and Edward Snowden I feel like I am missing critical parts of the information needed to stay informed. Is there a service or a site that is out there to be better informed about these and other civil liberty issues?
Edit: The Peter Maass story was here actually and I did read it, but the question still stands.
Is there a service or a site that is out there to be better informed about these and other civil liberty issues?
You have found it. There are others that have been writing stories as well, especially wrt NSA – Bart Gellman at WaPo, Spencer Ackerman at the Guardian, etc. But over the years, I have found Greenwald et al to be the most informative place to start.
I frequent the following in trying to stay informed:
https://freesnowden.is
http://www.emptywheel.net
http://www.cryptome.org
Democracy Now
ACLU
Techdirt (search on NSA or Snowden or ???)
In a sane society every employee of the NSA would be executed to prevent the Stasi State virus from spreading.
In a sane society there would be no executions at all.
Executions would be far less common if the jury that sentenced death also had to execute.
Little authoritarians believing in in the apotheosis of the state amount to little more than little Caesars with their thumbs down and clean hands.
I want to see jury members waking in the night remembering what they have done and seen, not some indifferent state psychopath banally following orders .
After all is said and all revealed, the one thing that will have the longest lasting, and possibly the most detrimental affects, but will in all likelihood receive the least attention. Will be the intangible drain on knowledge such a massive and ubiquitous system requires. The NSA is the largest employer of mathematicians in the world, it also employees a vast network of computer scientists among other talented individuals (It Trolls Hundreds of Universities). By taking these intelligent individuals and turning them into voyeurs and voyeur enablers, the surveillance state has not only destroyed our privacy, but also perverted a portion of our future. What could have been discovered, created, and built by these individuals, had they not been seduced into a life of convenience and luxury (building databases, Etc. doesn’t require a whole lot of critical thinking and Snowden was making upwards of $100,000). The lasting effect of this will be intangible, but surely great.
What may have been had all this potential and knowledge gone, not to exploiting the present, but rather building for a better tomorrow?
Links*****
NSA Employment/Recruiting:
http://www.scientificamerican.com/article/mathematicians-and-computer-scientists-shrug-over-the-nsa-hacking/
I didn’t even think of that, very good observation. It really gets you thinking and what really burns my ass is that this is all taxpayer funded. Billions of dollars going to watching people on the internet while kids are hungry and living in squalor and schools are shutting down. It really bothers me what the governments priorities are.
I share your disgust and disappointment. Trillions, not billions, of dollars have created spying and warring entities while basic human needs such as food, health, housing, jobs, and clean air and water have been cruelly neglected. We have a government that works only for itself. It is a greedy evil soulless monster.
^^+1
The drain on knowledge required by NSA activities sets up the scenario for an oppressed population under the forced control of global government.
The US labor pool is zero-sum. There is some 20+% of US GDP generated by governments. By diverting massive resources to feed the organization into a monster, we are on our way to creating a psy ops nightmare.
Check out some of the federal contractor job websites such as icfi.com, battelle, etc to see the vast resources being poured into spy ops activities. It makes me sick to see how a culture of surveillance has gotten a stranglehold on the general population.
People who think public key encryption can save them from government snooping are delusional.
It make keep credit card scamers at bay but the government snoops us all the time.
If you need secure data links then a code book must be physically transported to and keep secure at all points in the data network.
All else is worthless.
National. Scum. Agency.
No Such Agency
Never Say Anything
No Sodding Accountability
New Stasi of America
Nazi, Socialist, A$$holes.
Everyone use Linux! It isn’t hard to install. You can tailor it to do many things. Linux is open source so if it tried to use backdoors, computer geeks worldwide would immediately notice and call it to our attention. Intel and AMD, the CPU chip makers have already constructed new back doors that Microsoft and Apple give the NSA access to. Linux doesn’t cooperate. I use Slackware64, Version 14.1. Linux isn’t super friendly, but once installed, IT IS ROCK SOLID.
Dream on. The data security features are almost non-existent Applications can dynamically alter the OS just long enough to unlock everything then put it back again.
Without hardware that can independently detect malicious references or alterations the data security offered by software is nothing but BS.
Yeah, except for the browser app you’re using. Did you read the article?
Linus, what you’re missing is that ANY OS that updates (inc. virtually all flavors of Linux) already have the NSA back doors built in. The NSA has seen to it.
Critical crypto bug leaves Linux, hundreds of apps open to eavesdropping
This GnuTLS bug is worse than the big Apple “goto fail” bug patched last week.
http://arstechnica.com/security/2014/03/critical-crypto-bug-leaves-linux-hundreds-of-apps-open-to-eavesdropping/
Feelin’ the love…. (?)
The mass inserting of spyware to defeat encryption has a home in most if not all sites like TI, the Guardian. I posted earlier regarding getting replies faster than even reading what I posted. To me its obvious a computer is reading my typing and sending a reply that appears to be triggers when I hit the send button. Up pops a reply!
So what is a humble Sys Admin supposed to do in response to such shocking revelations?
Our small firm has contracts with corporate clients that make us responsible for defending against disclosure of Confidential Information we may hold or have access to on behalf of our clients. We are obligated to file a “Security Incident Response Plan” in the event of a breach, or “a reasonable expectation of a compromise of the security, confidentiality or integrity of data or information under control.” These are standard boilerplate contracts.
Based on your article, it would appear that nearly every tech corporation on the planet needs to inform their clients that we can no longer guarantee the confidentiality of their data, and need to invoke indemnification under an “Uncontrollable Forces” clause (if we are fortunate enough to have one). For example, ” shall not be liable for… any cause beyond its reasonable control such as… war, sabotage, act of a public enemy… provided that promptly notifies in writing…”
Are other firms with in-house counsel already doing this?
Glenn/Ryan, I’d like to see more analysis on how major tech industry firms are responding to the risky legal situation your revelations have raised.
That is an excellent idea! Some people are not following this very closely or they assume it is governments spying on governments something to bring it a little closer to home could be useful in the fight. It is probably more safe for some people than my idea of hacking the NSA, GCHQ, and friends employee list and letting the community know who and where the traitors of the people are. I still think we should cut off the water supply to places like PRISM though and let their servers fry.
When this agency has RSA on its payroll, taps trunks, coerce providers, use secret courts, its not about security, its the thrill of the hunt. Again “they” will say I was following orders as millions have before.
In my humble opinion, the more transparent and upfront you are to your clients about what you do and do not have to do is the way forward. Integrity is what people are really craving in today’s world – beyond contracts and the so-called ‘law’.
Never use facebook.
Nor Google. Nor Microsoft. Nor Apple. Probably a bunch of other American companies as well that have provided back doors into their software. But at least those four are certain.
Never look up.
I wish Steve Jobs was alive and running Apple. He may have been enough of an idealist to have told the US government hands off. It appears only small companies like Ladar Levison’s Lavabit have a “spine”. What new revelation will it take for a large US company to tell the US Government to “pound sand”?
Dates in the article for “blocking” maybe for the specialized current blocking, but it began in the later portion of the 1990′s. The resurgence of blocking lately seems to tie well with lil clapper lying to congress. In my experience it has never ended(since 1990′s) but has spiked numerous times and likely higher since the lying to congress of late.
Whoa, big time revelations here. I am starting to see the rest of the picture with this round of documents. Not only does NSA/GCHQ want to monitor and infiltrate targets computers they also want to play big brother with what seems the entire internet if they aren’t doing that already. What a great intelligence gathering position to be in, at the arches of the information network, collecting and monitoring whatever the NSA wants. Goodbye internet
We’re back to the Neanderthal days, where now our amygdalae once again rules over any rationality we may have gained in the thousands of years we’ve been walking upright on this planet.
From Quinn’s “A Day of Speaking Truth to Power” – https://medium.com/quinn-norton/dbc0669aa9ca
Not really surprising, I’d thought of this kind of thing years ago. It’s an obvious problem with having a computer (or smartphone) always connected to the internet.
Also: it’s a pretty clear way to track some internet use by those using the TOR browser, or other proxies: fake the server, put a server in the middle, or spy directly on the source of the TOR use, your computer.
The policies of Google, FBook, MicrosSoft, Verizon, ATT, Sprint, TMobile I’m sure, don’t help. So in these regards Yahoo and Blackberry both come out of this looking a bit, only a bit better.
Groundbreaking surveillance technology ? Gee, the next thing they will do is call the program ‘bots’
Why, the NSA has made all the way into the 90′s with their groundbreaking surveillance technology.
Sort of agree, this is probably a distraction from what’s possible, and being done.
No, I don’t mean that Greenwald and The Intercept are paid agents of this conspiracy.
Is it any surprise that CIA spied on US Senators after forcing those Senators to use CIA supplied computers to read classified docs?
Don’t worry about this; the government will only use this on its enemies.
Worry that your government thinks you are its enemy.
Based on this behavior of making 1984 a reality, it is impossible not to be the enemy of the NSA. They will of course call on us to unilaterally disarm.
This is all nothing short of complete power and control of the world’s population for the purpose of enslaving that population.
Once enslaved we have no place to run, no refuge from the tyranny. Exactly the same senario as slaves since millenia.
The NSA is following orders of Israel. If you wan to see your future, just look to the Palestinians.
Outstanding work, Glenn and Ryan. You guys are getting really good at presenting these complex and convoluted stories.
Also, it’s encouraging to note that the reporting here seems, if anything, rather less constrained than in other fora. A very good thing.
Now I’m suffering from code name overload!
TURBINE … UNITEDRAKE … CAPTIVATEDAUDIENCE … GUMFISH … FOGGYBOTTOM … GROK … SALVAGERABBIT … HAMMERCHANT … HAMMERSTEIN … QUANTUMSKY … QUANTUMCOPPER … WILLOWVIXEN … QUANTUMHAND … SECONDDATE … FOXACID … VALIDATOR … TURMOIL … TUTELAGE … INSENSER … QUANTUMTHEORY
It’s just a matter of time before the gov’t/NSA/military decides to begin massive censorship of the internet and to close sites at will if they advocate “freedom”. There goes your freedom of speech.
“……There goes your freedom of speech……”
Yea. There it goes. Have you seen any evidence of that yet??
My, what short memories we have here!
https://firstlook.org/theintercept/2014/02/24/jtrig-manipulation/
https://firstlook.org/theintercept/article/2014/02/18/snowden-docs-reveal-covert-surveillance-and-pressure-tactics-aimed-at-wikileaks-and-its-supporters/
Just to give two examples. Plenty more examples available on request.
I believe that the tactic in of the United States is not to openly jail and ban viewpoints; it’s tactic is to let you say what you want and then persecute you if you say something that is not approved of.
“……..I believe that the tactic in of the United States is not to openly jail and ban viewpoints; it’s tactic is to let you say what you want and then persecute you if you say something that is not approved of……”
You really shouldn’t confuse free speech with an individual releasing information that is clearly in violation of the law and in violation of the non disclosure of information he was required to sign while he worked for the NSA as a subcontractor. Snowden lied to his employer to get his job. He specifically applied for the job to steal the documents. He stole far more than necessary to get his point across and now he has chosen (and I mean chosen) to live in an anti-democratic country to avoid prosecution.
Assange, who has also released an abundance of top security documents, is wanted for questioning in Sweden for the assault of two women. That must be a new form of freedom of expression. Who really even brings it up his assault charges anyway? Far left wingers are far to infatuated with Assange’s attempts to discredit the US government regardless of what he might be charged with in connection with two rapes.
Already going on. Notice how various Corbett Report clips and other youtube videos have audio that just drops out during key parts. And did you ever notice on Reddit when it says something like “45 comments” but you click in to it and there are only a handful?
Just goes to show change to the entire political structure must be made. The controllers are finding ways to keep their advantage in a new digital age where more and more ordinary folk are waking up to the shenanigans that have been perpetrated on the world for eons. With this technology and robotic technology, humanity is shifting to a very ugly world, one controlled by the traditional narcissistic “powers” that be. On the other hand, they don’t know anything about computers and have to use the computer savvy. When we disempower the controlling parasites, humanity can herald a golden age – we can use this technology for our edification instead and accelerate our evolution.
“One implant, codenamed UNITEDRAKE, can be used with a variety of “plug-ins” that enable the agency to gain total control of an infected computer.”
Oh reeeeeeeealy? UNITEDRAKE you say????? Oh how you all must just sit back and laugh and laugh during your wordplay. Listen up kids – that’s childplay compared to what’s headed for your cribs. Just wait until YOU are being raked over the coals by THE UNITEDPITCHFORKS OF AMERICA with a variety of plug-ins that enable OUR agency to gain total control of your every infected and collective orifices!!! I know how to use my words too…
Ok, you bring the pitchforks and I’ll bring the guillotines!!!!!
@bloodypitchfork … I think wolfess just called your name. Can you bring your guns – and your cute little wolverines, too? Pretty please????
http://sipseystreetirregulars.blogspot.com/2009/08/son-you-dont-poke-wolverine-with-sharp.html
I understand the calls to fire the brass……. Its just that you can imagine how these things get so out of hand.
There is this important job to protect the nation. There are threats all around the world and even on home soil. You put these super smart and ambitious people in charge of finding out ways to find out what the bad guys are doing. They look at oversight as red tape. Its just a pain in the rear. Its the government stupidly getting in the way of itself. Its hamstringing efforts to protect Americans. I doubt that they consider very much the ramifications of what they are doing. They have a job to do. Its an important one, and one that they believe in.
There are all sorts of problems with this narrow thinking. The one I find interesting is the given by Mikko Hypponen at the beginning of the article.
Forget about our freedoms and liberty being violated (Flippant, I know). It sounds as though Mikko Hypponen can very reasonably argue that deploying all of this malware could make the internet less stable. It could create more holes for those with bad intentions to do harm to Americans and American government.
As far as how Greenwald is choosing to release the Snowden leaks, I think its smart. All of these new revelations are hard to digest. By bringing them out bit by bit we can force the government to answer very specific questions about very specific actions. We can very specifically catch them in lies, which has already happened. If everything were released at once, I think that important details could be thrown out too easily. The administration could answer a simple question about malware, and when a more difficult question comes up they could simply say, “We’ve already addressed that. If you want that answer please refer to this or that response that really won’t tell you anything about the question you just asked, but it can sort of pacify those listening enough while we move onto something else. Next.” Having these revelations role out more slowly is causing them to have a greater and lasting impact.
NSA owns the net, yet when Russia, a country, not a tipster, warned the US about the Boston Bomber, the US did not have enough resources to fully evaluate him.
When the father of the Underwear Bomber, walked into the American Embassy, and told them his son is dangerous, the US did not have enough resources.
The US would rather lock-up forever the Fort Dix 5, who were totally innocent of terrorism,
then go after any real suspects.There is a need for real suspects, with warrants, to be under monitoring.Till this happens, I can’t see the NSA as anything more than Security Theater, like the TSA does at airports.
It is very difficult anymore to separate the good guys from the bad guys. I fear I am going to wake up one day and find that I live in the former East Germany or Soviet Union. The government at all levels needs to get the heck out of private citizens lives.
Maybe because there’s no such thing. There’s only guys, with different interests, values and worldviews, some with a bit more of a sociopathic personality than others. Plus a lot of this is not individuals doing stuff. It’s bureaucracies that act in certain ways for the benefit of the concentration of power, both financial and political.
“skillz” is not a sic btw. It’s hacker-speak for tech skills.
That’s why “SIC” means, “spelling is correct”. It is explicitly to point out an unusual word is not a typographical error.
Actually “sic” is meant to show that a word was written as shown, regardless of being spelled correctly or not… short for sic erat scriptum or “thus it was written”
“sic” also means “this alternate spelling is a disturbing window into the sick minds at the NSA”. The spelling speaks volumes about the professionalism and emotional maturity of the analyst in question.
The NSA analyst (probably a white male with a crew cut and wearing a suit) was thinking “We [NSA] da baddest gangstaz in da hood!”
It is Latin for ‘thus’, i.e. ‘it was thus in the original’ and indicates that the preceding word was incorrect in the original, and is not an error of the present writer.
My family was brutalized via NSA supplied data Sept 11 2002. Multiple events. It was a mistake. Are there documents identifying individual innocent victims that can personalize the big picture?
The use of the phrase “foreign targets” is used repeatedly throughout the article, but what really does that mean? It implies, I’m guessing, that these techniques aren’t being deployed against US citizens, but aren’t US citizens, in the minds of the UK or New Zealand for example, considered foreign? Of course, exempting US citizens doesn’t make it any more acceptable, but I would really like to know what the phrase means in the context of the NSA directives.
The U.S. citizens are snagged by GCHQ and the Aussies.
I think the answer to that is in the NDAA that Obama just signed. It gives them the power to lock up Americans without charges for as long as they care too. But Barry promised not to use it, so don’t be alarmed. It also legalizes the use of propaganda on the American public. Not that they haven’t for years but I think it is telling that they have made it the law.
To paraphrase Victoria Lebensraum, Duck EU’All ! Das POTUS’ halfascist Adolphbet strudel agencies are already malwaring US DOMESTICALLY!
“The intelligence community’s top-secret “Black Budget” for 2013, obtained by Snowden, lists TURBINE as part of a broader NSA surveillance initiative named “Owning the Net.””
Translation: They declared a Technology War against this world and used our own fucking computers in the warfare to shoot ourselves in the face, ass, hearts and heads out. And then they sat the fuck back, poured fucking shot of Crown Royal with a plate of caviar and melba toast … and sat back watching us whore ourselves out in their twisted version of internet porn – then got off on it! At least Quinn Norton got to LITERALLY call them “creepy fuckers” to their face: https://medium.com/quinn-norton/dbc0669aa9ca (thanks @TallyGoGazehound for the original link!)
These fuckers are ALL grand fucking poo-bah’s, imperial brethren, and card-carrying members of the Jeepers Creepers Fucker Club.
Let’s see if we can make a simile here. The difference between today — this administration and the Internet — and the 1950s — the Eisenhower administration and the Interstate Highway System — is that Ike didn’t rig the Interstates to collapse in the name of national security.
That about right? Because the one sector of the US economy that worked now has more holes in it than a Gruyère cheese. That is no highway to prosperity.
BTW, Congress, get out your textbooks and turn to Art. I, Sec. 8, clause 3: “The Congress shall have power … To regulate Commerce with foreign Nations, and among the several States …” CON-GRESS, you idiots, not Fort Meade. Remember that the next time you want donations from Silicon Valley.
Precisely.
CONgress is acting like a gawddamned neutered capon, when in reality, they have the power of the purse. If they wanted to stop this nonsense, all they have to do is suck it up, grow a set of knutz, and slash funding 100%. Cripple these c*ocksuckers in their tracks. Shut off their power, and water, and gas, and let them sit in their cube farms in the dark.
They’ve almost all been spied on and found to have skeletons hidden away they don’t want exposed – that’s the stick. The carrot is the riches they will acquire if they don’t complain.
Well, seeing as they are US citizens, regardless of how crooked they may be, I guess the “Foreign targets” have never been that “foreign” at all, huh?
Knowledge is power, the internet now contains most of the knowledge in the world, most of what’s left lies on personal computers. Now the NSA has been in control of that power for over a decade, and all they have to do now is sit back, push the button, and watch how their nations swing in the breeze like fucking wind chimes.
The 5 eyes alliance: Controlled by their own spies. I guess we now knows who watches the watchmen when they don’t watch themselves. So I guess the new question is, do these fuckers realize that the power they hold could destroy the world and do they give a fuck?
As I recall the original solution to the watchmen problem was to tell them that if they didn’t do their job, the world would end.
These guys know that to be a lie. They could do their jobs and *cause* the world to end.
That being so, there’s still my point about damaged commerce. You’d think that Congress would look at their campaign-finance reports and see who’s damaged by an Internet so compromised that no one will buy products, goods or downloads over it any more.
They might not care about the Bill of Rights, but if they won’t enforce the Commerce Clause — the Silver Chalice of American law — then Americans are screwly trued.
Did you not read where it said they would monitor those labeled as “extremists”? I wouldn’t go quoting the Constitution unless you want to wear a label. You know they already send the IRS and the Justice Department after other groups who Nancy Pelosi gave that label to.
If the Commerce Clause is subversive or extremist, then we really have gone through the looking glass.
If this comes as a surprise to anyone, then I can only say “wake up and smell the roses”. Did you miss that all US software and cloud services have backdoors (even Microsoft….), anyone using Firewalls from Israel or even Antivirus from Russia? There are plenty of choices for security products made in Germany, that do have a no backdoor guarantee and adhere to some of the strongest privacy laws worldwide. The time has come to take action and things in your/our own hands.
Not funny. The brilliance of such minds being used for such deviousness. How can these people live with themselves, with their families, in their communities? Soiling us all.
Some folks will do anything for a buck.
They wrap themselves in the Flag, and the tattered Constitution, and convince themselves that they are “Patriots” and “Freedom Fighters”. Protecting US all from their fabricated boogey-man named Al.
Al K. Ida.
Half of these “intelligence” people were recruited from the criminal world. The ultimatum left to the hackers is either your with us, or against us. The good news is that I am sure with the help of these documents, many a new hacker are avoiding the NSA like the plague, thus effectively reducing the size of the NSA by default.
“The system would relieve the user from needing to know/care about the details,”
I’m not on your fucking “NEED TO KNOW” list you conniving pieces of shit. Have you forgotten in your big Pharma-induced coma that YOU answer to MY ass! And to ALL the rest of US!!
Don’t you dare sit there and tell us pat us our fucking heads and rub our fucking bellies then call US crazy!!!! Now let’s just see who are the inmates in MY fucking asylum!!!!! You don’t even deserve padding the cell.
Don’t hold back.
Tell them what you really think………
I’ve only just begun… Don’t piss off a red-headed Irish chick. Our DNA is as tender in love as it is lethal in war. We whisper little strategies to our men and feed them breakfast before kissing them as they leave for battle against our enemies. And we’ve got our God, saints and angels to back us up. And who pray tell our little counter-spy in all this? Why it the Devil himself. They left that part out of the bible … and I know for a fact – there WILL be hell to pay. And I’m just over in my little ‘ole kitchen … building a little fire in oven … making dinner … waiting for MY man to bring home the bacon. Thank God. Amen. Good night fuckers!
Um… this is awkward. Punctuation is everything and most of the time I barely know what I’m doing. Even I’m blushing over the potential impact of that last line because I don’t know when to/not use a comma properly. Take that line anyway you like, but FWIW – I would never say anything too profane. SRSLY – I am a lady!
As a red-headed, Irish blood-blended male. I get your drift.
Hah!
@Geoman… Hello my fellow Spud lover. Those douchebag fuckers – don’t they know the Irish LIVE for this shit? Bloody Mc’s are kinda relentless that way! Our entire culture was born of politics, war, family and our fellow countrymen. Poetry is still read in every pub, sometimes choking back tears telling all about our legends and lores … as we sit silently hanging on every word. We get pissed ass drunk listening to haunting wails of pipes … and to songs with melodies so sweet it takes your breath way … of our grief … and of war … until we crumble and weep.
The next day we get up, have a pot-luck and get pissed ass drunk dancing jigs on the graves as we swear an oath to avenge that death, their honor, and their bravery – even if it kills us to do it! And we throw the best damn wakes IN this town! But It’s – always -the – fucking – politics – that picks the fight to start party again. Every. damn. time. We only fight each other to warm up – but we always have each others back in battle, right?
Hell hath no fucking fury as a woman scorned. You guys can have all the rest of them – but I am saving my darkest prayers for the devil himself to personally show no mercy to all the double-crossing, no-good, lying thieving, peeping, torturing, SOB – Irish – Em-Effers who stood with England in this battle while they hocked loogies on those graves of my ancestors. And especially for those that are suffering for it that are living today.
Psst – NSA – BTW – I’m Irish AND American. And that’s not your heartbeat – think of it as the throbbing Michael-Flatley footwork before you make it YOUR grave… Good night. Amen.
Although, of course, the actions of these spying agencies are indefensible, I believe a fair amount of the blame should also be levied against the tech industry (silicon valley). Spy agencies are created and designed to spy. That is what they do, and so we cannot be shocked when they devise invasive spying programs for internet data. What is completely inexcusable is the absence of better encryption and firewall protection built into the existing programs that we purchase and use everyday. Where is Google, where is Apple, where is Microsoft??? What the hell have the so called computer genius “developers” been doing? All of this NSA news has led to a complete failure of Office 365, as most corporations cannot trust or use this software. This even led to Microsoft changing their CEO. I’m glad they have taken a huge hit and feel that all of these major tech companies are in everyway complicit, have egg on their face, and should be ashamed of themselves.
I don’t know too much about this stuff but I am very interested and it is clear to me that we have very power hungry Governments around the world. People saying there are spying activities going on in other countries that are just as significant are probably right, but does Greenwald have that information? No, he has the NSA files. Why should he release them all at once, that wouldn’t be very effective in creating a transparent government because the public would never be able to comprehend that much information.
Sooooo…… WHO failed to see this coming?
the FaceBook stuff is a given…since 2009
I am sure the all-seeing, all-knowing brilliant minds in government service had conceived of the need to control or eliminate citizen communication long before the unwashed masses had a clue, but Iran’s little Green Revolution using social media so effectively, surely motivated them beyond mere ‘war-gaming’. How many months after that became obvious did we have the nationwide cellphone blackout, which was advertised as some sort of “test”.
This is mind freaking, I thought Bad Guys are compromising the networks, but never thought of the government.
nsa malware aka microsoft windows.
“(humans tend to operate within their own environment, not taking into account the bigger picture).”
I guess these kids forgot they were human too. Maybe they should taken into account the bigger picture of what they were perpetrating against other humans while handing out business cards. They sure as shit didn’t take into account how that would factor into their picture. TERROR???? This is very own God damned, come to life, ZOMBIE TECHAPOCALYPSE!!!!!
Keep painting the picture Glenn. There are a lot of art lovers out here who love your work and who will come to appreciate your talent and technique. I can only draw stick figures, some people cartoon and “some people” are idiot savants … and you are the great master in this renaissance. Thanks Edward Snowden for providing the paint. And TI the brushes. This shit is PRICELESS!….
I failed to give credit to Mr. Gallagher. I apologize. As I myself am Irish too. I take personal delight in your name. St. Michael is answering my prayers so I don’t think it’s a coincidence you are a fierce warrior in this battle. Thank you.
CORRECTION: As I myself am Irish too I take personal delight in your name.
Jeesh! Talking is so much easier … proof-reading and punctuation is a tricky business.
Hardly surprising, for godsakes, given the kind of money spent on all this NSA shite, that the USA has so little cash left over with which to restore its crumbling and collapsing infrastructure. — As for GCHQ, I wonder whether any VAT and corporation taxes get paid on all its US $ profits into the UK’s public purse? — BTW, I am inclined to think that GCHQ will already by now have lobbied the OED to redefine the word “hacking” as synonymous with “owning” — but only if and as and when GCHQ is itself the subject of the verb.
The government prints money and can have as much or as little as it wants to have. Programs it likes never want for money. Programs it does not like quietly get defunded. And which ones meet which fate are far from accidental.
Yeah, thanks for the feedback. I’ve long maintained that the ever-expanding, ever-encroaching NSA is actually no more than a ponzi-scheme, not worth the paper it’s written on in terms of the promised dividend — viz., so-called terrorists.
“The intelligence community’s top-secret “Black Budget” for 2013, obtained by Snowden,”
In a one sentence paragraph, near the head of a long article. Way to rivet one’s attention, Glenn.
Indeed. Do tell us more.
Time to fire all upper management of the CIA & NSA including Generals, who should be busted & dishonorably discharged, with no pension & then prosecuted ! We should all give them the one FINGER salute as they leave & tell them to sit on it and rotate !
Disclaimer: Be advised it is possible, that this communication is being monitored by the National Security Agency, GCHQ or other third party organizations. I neither condone nor support any such policy, by any Government authority or organization that does not comply, as stipulated by the 4th Amendment of the U.S. Constitution.
“Time to fire all upper management of the CIA & NSA including Generals, who should be busted & dishonorably discharged, with no pension & then prosecuted ! ”
Nah, thats not going to do anything. Time for Ron Paul’s idea-simply eliminate huge departments of the government. The CIA should be the first to go.
Of course they’ll never actually do anything like that because America is a completely paranoid nation whose fear of foreign threats is waaaaay greater then the fear of a police state.
This is a masterpiece! Thank you!
If one has ever been on the receiving end of the aforementioned attacks, the veracity of this information and scope of operation can not be questioned.
Essentially you are screwed if you are using any Operating System (OS). See Selector types above and note Windows Update ID’s and Windows Error ID’s. Dumping your OS will not help because as soon as you register the new one your screwed again. Here are some tips that will REDUCE but not alleviate NSA access to your machine.
Do not allow firewall exceptions.
Always clear browsers and temporary internet files. Do this frequently. Configure your browsers wisely.
Load Malwarebytes.
Run an AV program that cleans content. Run additional programs that clean content and/or Registry entries.
Run an IP Blocker program.
Do not allow Windows Update to load updates automatically. Choose to manually update.
Check your Services carefully. Disable all of the ones that enable NSA access such as Remote access services.
Manually pick over your registry from time to time.
Stay off of social networking sites. This is paramount.
Use Startpage as your Search Engine as opposed to Google or Bing and delete their entries from your registry.
Print rather than download.
I am not a techie but I have found the above listed things to minimize machine problems caused by NSA intercepts. Please keep in mind that even these things will not alleviate the problem. If you are using a machine online you are screwed. Yup….it is us against them but we have numbers on our side. It is NOT their internet.
Thank you once again for publishing this excellent article.
“Stay off of social networking sites. This is paramount.”
In a sense, isn’t that what we are all doing here, networking?
Although it is a given, that this site in monitored all day, everyday………….
(No need for a response, I was being sarcastically rhetorical)
But hey, anytime I can ridicule those fools, it makes my day.
Yup….but it is a calculated risk in the formation of opposition.
I most definitely appreciate the finer arts of the “Lock and Load” mentality. Drive on CitizenSane!
Ha, by using a closed sourced OS like Windows your screwed anyway, you can be sure that things has built in backdoors. So your counter measures above, while good practice, will not stop the like of the NSA if they wanted.
To have the best chance of security, you must at least start with a open source OS, plently of Linux/BSD stuff out there a hell of a lot safer then any MS OS
You speak the truth. I wonder why nobody else in this thread mentioned Open Source Solutions …
Seriously?
Linux was in part developed and is widely in use by the DOD. Check it out.
Sure…just use the DOD servers! Make it easy for them….
Sort of like jumping out of the frying pan and into the fire.
An option yes, but no thank you.
Um… this site and the comment threads ARE social media. I’m a middle-aged old dame who’s been around the technology block so even though these not my FB friends (closed years ago) and I don’t tweet them (twit speak gives me seizures) – there is no doubt in my mind that as we gleefully socialize here – it is – in fact – social media. The NSA is hanging on our every word. Everywhere and on any piece of technology you use. Today – they own the EVERY technologies’ ass. It’s up to us to kick theirs before they screw us to the wall. They’ve been shelling out our tax dollars for military grade equipment and selling their cast-offs to any local law enforcement agency that will take it at a discount – then provide training – double dipping your tax dollars to do it. Wake up dear. And after you do … doublecheck those numbers again. Please. Cuz your numbers are way off if you think any combination of virus protection has any chance to stop this shit.
It is unfortunate that the techs working at the NSA are enabling all of this. It used to be something to be proud of to work for the NSA. Now it is just an embarrassment.
How many former NSA techs have to lie on a resume about where they used to work. Just remove NSA with McDonalds and you have more credibility.
Mr. Greenwald and Mr. Gallagher
Do we even know if the US and the UK are the leaders in this kind of technology worldwide? Could it be that US rivals like the Chinese and the Russians could have surpassed US capabilities? In the digital age, cyber warfare is becoming a much more important tool for intelligence agencies. Malware has been used to attack the Iranian nuclear program, and certainly, cyber warfare has been used by all intelligence agencies to gain access to defense contractors and other companies that develop technology used for military purposes. Cyber warfare is being used by both sides in Ukraine and shows the importance of intelligence capabilities to ward off and to access computers for future conflicts.
“……..U.S. intelligence analysts are closely watching the roles hackers are playing in the Ukraine conflict for clues to how Russia and others might employ cyber capabilities in future conflicts, said two U.S. officials who spoke on condition of anonymity to discuss intelligence issues. The officials said cyberspace is quickly rivaling traditional battlefields as a place where wars may be won or lost…….And on Feb. 23, state-funded Voice of Russia published e-mails alleged to have been written by Vitali Klitschko, a pro-Western candidate for the Ukrainian presidency. The documents leaked by a hacker group calling itself Anonymous Ukraine included one in which Mr. Klitschko thanked an adviser to Lithuania’s president for funding the Ukrainian protests……”
Of course, our whistleblower in Russia is likely right on top of Russian intelligence hacking into systems to expose their covert violations of the Ukrainian email system(?).
Aside from the so called violation of the Fourth Amendment by the NSA, do Americans (or anyone for that matter) understand that they are giving up privacy willingly and without their knowledge on a daily basis – and that this is a result of living in the digital age? According to 60 Minutes which aired last Sunday:
“……Over the past six months or so, a huge amount of attention has been paid to government snooping, and the bulk collection and storage of vast amounts of raw data in the name of national security. What most of you don’t know, or are just beginning to realize, is that a much greater and more immediate threat to your privacy is coming from thousands of companies you’ve probably never heard of, in the name of commerce…..They’re called data brokers, and they are collecting, analyzing and packaging some of our most sensitive personal information and selling it as a commodity…to each other, to advertisers, even the government, often without our direct knowledge………..[a] multibillion dollar industry that operates in the shadows with virtually no oversight…….Companies and marketing firms have been gathering information about customers and potential customers for years, collecting their names and addresses, tracking credit card purchases, and asking them to fill out questionnaires, so they can offer discounts and send catalogues. But today we are giving up more and more private information online without knowing that it’s being harvested and personalized and sold to lots of different people…our likes and dislikes, our closest friends, our bad habits, even your daily movements, both on and offline. Federal Trade Commissioner Julie Brill says we have lost control of our most personal information…….”
It’s fairly pathetic to focus on the NSA without acknowledging that today privacy is an ongoing issue in all walks of our lives. This area would seem to be a less destructive use for whistleblowers.
All valid points, and I would add that, given the amount of private consumer datamining, we now have troves of data, and like any treasure chest, it can be stolen. Certainly this kind of NSA lock-picking means a lot of compromised systems for crooks, not to mention foreign gov’ts, to exploit. The attacks on systems administrators in particular is not going to protect either commercial or national security, either from petty theft or a surprise cyber-attack.
You’re right about the US/UK pioneering this kind of technology, in the same sense that the US pioneered winged aviation in the last century. Unfortunately, other countries can adapt that technology and teach us a thing or two about national security, as we found out in Hawaii one Sunday morning. We even had the tech to see it coming, but …
- – -
Radar Operator: Sir, this is Private Elliott at Opana Point. There’s a large formation of planes coming in from the north – 140 miles, 3 degrees east.
Duty Officer: Yeah? Well … Don’t worry about it. (click)
– “Tora Tora Tora”
“…….You’re right about the US/UK pioneering this kind of technology, in the same sense that the US pioneered winged aviation in the last century…..”
Personally, I think you are winging it. Needless to say, I never said or implied that we developed the technology. I doubt anyone knows for sure what the Russians and Chinese have developed on the cyber-games front. Russian interception of emails just indicates that the Russians have developed similar technology. Chinese hackers have attempted quite successfully (at times) I suspect, accessing US military applications. It’s certainly a worry. Now, of course, our enemies have the advantage. Nothing lost though really, eh?
“……..Certainly this kind of NSA lock-picking means a lot of compromised systems for crooks, not to mention foreign gov’ts, to exploit……”
The key here is that there is a huge amount of personal data that is compromising our privacy. Much of the data we give with our permission to Google and others who sells the data to advertisers who rumble through our email etc. The NSA might be overstepping the Fourth, but it’s the tip of the iceberg. Clearly Snowden must understand this – as does Greenwald so is this really an issue of privacy with the NSA? I doubt it with Greenwald. Most of what he has written has been in opposition to US policies (and Israel). It was ironic that he cited Russian TV for freedom of the press (by a reporter stationed in Washington DC where she cannot be beaten or killed). I’m not sure what the difference between the two might be since they both focus on US policies. Maybe RT is a sister station?
What if all this backdoor hacking has compromised our commercial and private software? Sure, the Russians and Chinese probably have tried it as well, but did we self-inflict?
Addendum to Dan Froomkin’s piece from yesterday.
What charles Pierce said:
Time to fire all upper management of the CIA & NSA including Generals, who should be busted & dishonorably discharged, with no pension & then prosecuted ! We should all give them the one FINGER salute as they leave & tell them to sit on it and rotate !
Disclaimer: Be advised it is possible, that this communication is being monitored by the National Security Agency, GCHQ or other third party organizations. I neither condone nor support any such policy, by any Government authority or organization that does not comply, as stipulated by the 4th Amendment of the U.S. Constitution.
With the content of the current article here, and the content of this article here https://www.federalregister.gov/articles/2013/11/18/2013-27343/special-conditions-boeing-model-777-200–300-and–300er-series-airplanes-aircraft-electronic-system I wonder if there are any overlapping issues, or is it apples and oranges?
Could the disappearance of the Malaysian Airlines Jetliner be a NSA experiment gone FUBAR….?
For Chrissakes, I’ve got drunk and lost my car, but it is pretty hard to lose a jumbo-jet.
Corporate media “lost” the plane, but someone never lost track of it.
For anyone who comforts themselves with the knowledge that the NSA only operates on Foreign targets, it’s worth pointing out that by sharing the technology with other countries, they can enlist their help in applying the same techniques to Americans.
How do I know I am hacked by my govt? Twice in the recent past I have gotten responses immediately after I posted a comment such as I am doing now. What I am saying parties are monitoring some of my computer time(s), and placing comments immediately following mine to discredit what I have posted!
Is this what we pay taxes for? Is this what we abide by the rule of law for? Are We nolonger Citizens?
My belief and observations regarding ‘facts’, we(The People) have LOST! And its time for a New War.
Note to Mr. Greenwald; Sir you do us all a disservice requiring identification. Let the Govt have to provide the proofs in Court, rather than allowing it to force you into being their means.
This explains why, when I turn my computer on first thing in the morning, I see a flashing neon sign that says “You are being Redirected”, and immediately the NSA Homepage pops up, with the icon “Ask Zelda”……..
/sarc.
You mean Ask Ni Hao
It’s extremely irritating having permanent cyberstalkers that just can’t escape from, isn’t it? Have they started stalking and harassing you outside of the web yet?
Maybe your stalkers are just women looking for some pen”s
Karmic Retribution = Turbine …
The NSA couldn’t even be satisfied by just any old fan … they needed a God damned TURBINE! At least there will be no fucking mistaking exactly in which direction the full force of responsibility and accountability will be pointed. I truly relish the day when the velocity of their massive, steaming, putrid piles of dung in the blowback of this circus will fill their drawers once again. And I PRAY to watch in on live TV at their sentencing. As they weep…
When my mother used to tell me “Stop crying or I’ll give you something to REALLY cry about.” that usually did the trick. So fellas, um … “Terror”? You don’t seem to grasp the meaning of that word. That’s why god gave us knees … so when they start shaking uncontrollably from fear … you KNOW you’re in deep. Who are your enemies, again? Oh… and the delicious taste of terror that I feel for you is making me hungry. I’m saving my appetite for dessert! Thanks GG & TI … for letting those sweet aromas blow first in the Turbine first. Terror….
“Terror”?
That is the definition of what they will ALL feel.
It will be their puckering strings clenching a full blown “Ten” on the pucker scale, when their collective sphincter’s shrink, as they gasp and gaze at the throngs approaching the Bastille………..
@Citizen …
The U.S./U.K. and God knows who the fuck else have DECLARED INTERNET WAR on the entire fucking world.
Snowden was generous to throw them bones … and they just minced his words. Then they tried to chewing asses out left, right and center to stop him? And GG, The Guardian, Assange and Chelsea Manning… etc.
I CAN NOT WAIT for my turn in this savory buffet line to savor the assortments of offal that will be served up. Then I’ll will lick their damn pork chops and suck every last last bit of flavor out of them! Then I’m going back for seconds. Terror….
The blowback is happening now(with Putin, China). Maybe the NSA realizes this and is going on the offensive. US can’t keep invading countries and fighting stupid wars. I hope no country does to us what US did to them. China is building up, waiting, until US done spending themselves silly.
Glenn,
Your statement “Under cover of secrecy and without public debate, there has been an unprecedented proliferation of aggressive surveillance techniques.” is an exaggeration without any context. You neglect to mention many previous and arguably more invasive surveillance methods used throughout history. Just as an example, the active SORM program used by the Russians.
Please stop controlling the release of these documents and adding your biases. Your only value is the fact you control this information. Without that control you’re another insignificant reporter. Who is the real winner in this whole situation? Snowden – No. The public – No. Greenwald – Yes! You already have and will profit more than anyone. You are attempting to control the narrative like you control the documents. This is turning into Glenn Greenwald self aggrandizing slow drip torture.
Slow drip? There were 12 top secret documents published to support the claims made in this article. Other websites may indeed be publishing larger numbers of top secret documents, but quality and context is just as important as quantity.
G-Man is right. He’s making the NSA out to be the boogey man without providing context about other nation state actors with equal or worse programs and events that got us here (thousands of murdered Americans). Russia just invaded Ukraine. He’s slowly released docs since last June. I can read them myself. I don’t need him to tell me what they mean. Why isn’t Greenwald publishing them wikileaks style with discretion (unlike wikileaks) and then just getting out of the limelight? He is turning this into his own business venture.
without providing context about other nation state actors with equal or worse programs
Why isn’t Greenwald publishing them wikileaks style
Do you see any contradiction between those two statements? If Greenwald published more NSA documents at once, how does that provide context about what other nations are doing? By publishing this story, Greenwald is giving the NSA an opportunity to respond. With their massive resources, I assume they know all about what other state actors are doing. So if they deem it to be in their interest, they can now provide as many details as they like it order to place what they do in the proper context.
However, two things are revealing – their silence and the fact that most of their efforts are devoted to offensive cyber operations. If other nations have equal capabilities, that would force the NSA to place more effort on cyber defense. So until someone produces actual evidence otherwise, I will assume the US and its five eyed cohort are the dominant players in this game.
Good point, ‘Tater; although I would argue that quality and context trumps quantity.
After all, isn’t that the NSA’s argument? They want bulk info acquisition, most of which is totally unrelated to the quality or context in which it will help protect our national interests.
It’s already been made clear many times over Glenn does not have exclusive access. Other journalists Bart Gellman and Laura Poitras also have the documents. As does the New York Times, ProPublica, Washington Post, and so on.
His usage of unprecedented seems accurate to me – there is no precedent for a global dragnet surveillance system with the aggressiveness and scale with which the Snowden archives detail.
Is this a joke? How is the public not a winner? Pathetic NSA apologist.
You are attempting to control the narrative like you control the documents.
Of course he is. That’s why he shared documents with numerous journalistic organizations all over the world: Washington Post, Guardian, NYT, Der Spiegel, etc. all have sets of documents given to them by that tightwad Greenwald. He made them swear they wouldn’t use them though. And Bart Gellman and the cadre of reporters who’ve been writing their own stories using these documents since almost the beginning of the revelations are sworn to only publish under Greenwald’s byline.
It’s positively devilish how he set this up so that he has sole control.
http://utdocuments.blogspot.com.br/2013/12/questionsresponses-for-journalists.html
Yup. Greenwald has controlled the shit out of these documents.
I suspect G Man can only have one of two agendas. (1) He is part of that Dump It All crowd that believes the average reader can sift through the minutiae on their own and make sense of it, and doesn’t believe Glenn should honor his commitment to Snowden. Or, (2) he full well understands the liability that Glenn incurrs by being a purveyor of classified documents – as opposed to reporting on them – and actively seeks for Glenn to incur that liability. The arrogance and hubris of the G Man is rivaled only by that of the NSA…. So, I’m guessing you can infer which of the two agendas I most suspect in the G Man’s case. Particularly, as you outline, the degree to which Glenn has gone to report on the documents he has, as well as the number of other journalists who have their own cache of these documents.
I’m not suggesting he dump it all. Selectively dumping without starting a media company that benefits him and releasing the docs attached to his articles. I, in fact, can read them myself. I believe Greenwald has biases that surface in his articles. Seems that is blasphemy on these message boards… Greenwald is now a millionaire. I mean…. hello world….Greenwald is not a millionaire because of this!?!? It’s amazing how many people here express hate for America when we live in a country that’s more open and works better than every where else in the world. I have lived in Europe, Russia and Latin America. Would the people here rather be ruled by Putin, corrupt Latin American gov’t or the Chinese communist party? I’m baffled by the herd mentality dominating these message boards.
How much are they paying you, G Man? Or are we witnessing the even more insidious phenomenon of self-delusion… Either way, I fear your flying in the face of facts won’t influence anyone here; The Intercept is a place of truth and light, where reason is adhered to and enjoyed by all. Your input is of course wholly necessary and encouraged (look at me go, J.S. Mill!), but sadly, uninformed and naive as the other replies demonstrate ably. I just had an urge to underscore a few righteous sentiments that I couldn’t resist
Thank you Jamie for your courteous reply. I still stand by my statements. I’m not buying his whole spiel. Agreed, other outlets have some of the documents but only 1 person controls the mother load. Times received 50,000?? Over 2,000,000 were stolen. Okay so another outlet has 2.5% of the docs? Give me a break. I still believe the way he is releasing these benefits him more than anyone else. His rationalizations are self motivated.
There are other programs not run by NSA, SORM for example, that make the NSA look laughable with the US’s respect for “rule of law”. SORM acts without any restraint.
I’m not going to jump on this train saying these revelations are all good. A lot of people responding here are also naive.
quote”You neglect to mention many previous and arguably more invasive surveillance methods used throughout history. Just as an example, the active SORM program used by the Russians.”unquote
ummmm, has some Russian whistle blower leaked secret Russian intelligence docs…or did your MilProp supervisor tell you that?
I actually found this to be a relatively straightforward article, with plenty of facts and quotes from many sources, and very little bias from the author. Just because the rest of the world is concurrently developing these types of intelligence programs does NOT mean that it is not unprecedented in the United States. In fact, this statement applies to the NSA as well as the SORM program you’re referencing. In the history of humanity, this is an unprecedented breach of privacy, and it is not up for public debate. That’s simply the truth.
Who breached your privacy? No one cares about your emails or data. Your data resides on a data farm accessible by someone regardless whether it’s a company or the NSA. It’s never truly “private” unless it’s flawlessly encrypted end to end. No one at Google, Microsoft or the NSA cares about your data. Get over it.
Others have already addressed your boiler plate remark about “control of the documents,” so I’ll address your remark about “insignificant reporter.”
Edward Snowden chose to reach out to Glenn Greenwald to work with because, obviously, he saw a lot of “value” in the work he had seen from Greenwald over the years leading up to making his choice. He chose Glenn Greenwald for the very reason that he had long been reading his work. So Snowden obviously didn’t choose him to contact about working with him because he saw him as “an insignificant reporter.”
Glenn and Ryan
Just an FYI – I think the link to the “NSA Phishing Tactics and Man in the Middle Attacks” is busted. I cannot access it from my ipad. It may just be on my end but can’t access through Safari or Chrome.
I’d love to know their definition of necessary and proportionate. That would reveal their true intent. Power is one thing, but what this surveillance gives the Authoritarians is the ability to control us in every conceivable way by manipulating the mundane realities of our lives, and ultimately by directing how and what we think, feel, and dream – if we are even permitted the subversive act of dreaming.
The degree of malevolence this document reveals is astounding!
Clearly, our Government has let US down.
Thank you Captain Obvious: http://www.youtube.com/watch?v=dIqRGrP0ttA
Aren’t you just full of wit this morning.
I am so happy that you have mastered that cut and paste feature.
It took me a while but I did.
Wonderful!
You could have a career at the NSA.
@JLS … Now that you’ve mastered C&P maybe you should call Rand Paul. He likes to cut and paste – I hear he eats the paste, too. You two should get along swell. Buh bye now!
This may be off topic, but should be of general interest. Edward Snowden’s live-stream session on Monday, March 10 at the South by Southwest Festival (SXSW) in Austin, Texas, had Impressive audience viewing numbers. These audience participation numbers are encouraging as Edward Snowden’s enlightening revelations and heartfelt recommendations are now being heard by a much larger audience thanks to the journalistic efforts of Glenn, Laura, The Intercept, and other brave folks like the organizers at SXSW who refused to buckle to government pressure. The number of live-stream viewers, like me, of the Monday, March 10, Snowden SXSW session have been compiled by the Texas Tribune. Here are their Analytics:
“Okay, the numbers are coming in — here’s a summary of Snowden traffic from various other sites’ embeds of our feeds, etc.:
Visits: 271,823
Uniques: 228,712
Countries 203
Desktop/Mobile: 82%/18%
Per the Texas Tribune spokesperson, the live-stream numbers above are for embed feeds from the NYT, The Guardian, Verge, and others.
The Texas Tribune live-stream viewers peaked at 50,000. However, they reported that the Antarctica viewership, and I quote, “was paltry”.
Journalist attendees, regular attendees and photos show that the multiple viewing rooms at SXSW were packed. The total theater seating was 7600 so the journalist attendee estimates of over 7000+ are right on.
Feel free to repost these viewership numbers to other sites. People need to know that the message on privacy violations, and the NSA/GCHQ, … mass surveillance systems’ unlawful and unConstitutional activities are reaching a larger and more engaged world community. I am pleased.
That is awesome news!
Where is the “NSA Phishing Tactics and Man in the Middle Attacks” document?
What operating systems does this malware target, and on what ratios?
I use firefox on a windows xp v3 computer and found the malware TURBINE and HAMMERSTEIN in my registry. I encourage everyone to use Run and type regedit, in edit go to search and type in TURBINE. I found both in Microsoft Search Assistant.
For those of you that play Lord of the Rings Online you WILL find a registry key for the term TURBINE because that the developer…you can ignore that one
You found these because your search terms are recorded in the registry. Search for BANANAHAMMOCK or WEDGIESALAD and you will find them in the same place.
” I encourage everyone to use Run and type regedit”
Well…. dang. I’ll just go hop on my unicorn pony right now and do that! Should I format C:\ after I’m done eviscerating my registry?
“I encourage everyone to use Run and type regedit”
If you want to know if your computer is infected why would you not look? By the way, how are things in Maryland?
AND! This is NO DIFFERENT than what the Chinese and Russians are working on, planing to do, or already doing at the present time and using against the rest of the world.
shhhhhh…..you’re scaring me! twit.
How do you know?
How do you know? Can you prove what you wrote?
This is NO DIFFERENT than what the Chinese and Russians are working on, planing to do, or already doing at the present time and using against the rest of the world.
Race you to the bottom! Tag, you’re it!!
It’s completely different.
China and Russia are both still totalitarian states that make no promise of freedom of speech and democratic rule.
America was founded by thoughtful freedom-lovers who specifically enshrined protection of those principles in the constitution. So when government agencies like the NSA violate our democratic institutions, that’s a big deal. When they get away with it, we get even more illegal and unconstitutional behaviour (see the CIA).
You hit the nail on the head.
As long as those Chinese and Russian boogeymen are not prostrate to the Five Eyes, I don’t think they do near the harm to we the people (US, UK, CA, AUS, NZ) as our own governments. We have power in numbers over our government, but our Chinese friends could greatly multiply those numbers (not to mention that our fascist governments can’t violate them physically as easily as they do we citizens/consumers). Maybe, “Anonymous Five Eyes” can help hold the Chinese state accountable to the Chinese people and “Anonymous China” can help hold the Five Eyes states accountable to their people.
Phenomenal? Awesome? Don’t think I have a word for this.
But, clearly, what Chris Soghoian and Ed Snowden said at SXSW: End to end encryption seamless and functional straight out of the box.
This article somewhat contradicts what Snowden said at SXSW. He claimed mass encryption could defeat bulk surveyance because the decryption effort would exceed the potential payback. But he described hacking (which allows the NSA to circumvent encryption by directly logging keystrokes) as a means for the NSA to collect targeted information about legitimate suspects. But if hacking is managed by software, as described in this article, which allows it to be deployed against “millions” of computers, it becomes a new means of mass surveillance which defeats encryption efforts.
The keys to this vast network of compromised computers will become extremely valuable. Who controls (and safeguards) these keys?
From the section of the article entitled “Circumventing Encryption”:
“The implants can enable the NSA to circumvent privacy-enhancing encryption tools that are used to browse the Internet anonymously or scramble the contents of emails as they are being sent across networks. That’s because the NSA’s malware gives the agency unfettered access to a target’s computer before the user protects their communications with encryption.”
I think it is grotesque to reveal all this stuff. It’s completely permitted for the NSA to exploit servers and invade computer systems of foreign governments, companies, and person. It’s what the NSA is supposed to be doing. These leaks go way beyond the original so-called whistleblowing on domestic spying. These leaks are harmful to our national security and tell our adversaries around the world what our capabilities are.
You really don’t get it, do you? Can you really read this, with comprehension, and not understand how vulnerable the NSA is making you to – say – the Russian financial mafia, for example? Do you not understand that those who might want to steal/scrape your passwords, bank account information, “identity”… have the ability to find and use these exploits without any of this reporting? Is it possible that entire sphere of understanding has escaped you? Or, is it that it’s just too scary for you to contemplate? In which case your cognitive intereference mechanisms serve you very well.
“You really don’t get it, do you? ”
Yes Tallyho..the MilProp Unit 12, computer 14 operator does get it. His post is living proof.
Grotesque is the mindset that allows this to happen in the first place, and then rationalizes it as an acceptable behavior. That the NSA is “supposed to be doing this” is the definition of institutionalized fascism that exceeds both the bounds of conscionable behavior, and, counter-productively, exceeds by orders of magnitude the tools and methods needed and necessity to protect our national interests – namely more human intel ind interaction to find perpetrators – and not more indiscriminate computer dragnets in an attempt to control the entire internet.
These leaks are harmful to our national security not because they tell our adversaries what our capabilities are, but because they show the usurpation of the Constitution, exceed any rational explanation for the need or efficacy for such intrusions, harm the integrity of the world wide web for all of us on the planet carte blanche, and supplant executive branch power over the power that belongs to the citizens themselves via their representatives.
These leaks go way beyond the dictate of any agency to protect our citizens from harm from abroad or from within, and delve into monkeying with the interconnected internet in ways that have no possible justification or rational for meeting the security needs of those they were designed to protect.
What this reveals is not the permitted spying you described, does it? It’s wholesale “Own The Web” infiltration by robot of millions of computers. That’s not permitted in the US Constitution.
I didn’t realize the NSA had special exceptions regarding the constitution. No, this NSA is not supposed to be doing this — no matter how hard you believe it. They are not above the law, and they should be held accountable.
Another brainwashed victim in the seemingly unending supply of government robotic entities.
Beyond what’s already been said, there’s a thing called Universal Human Rights. See, everyone, not just Americans, have a right to privacy. (I know, that’s such a radical view to hold, I’m probably in a target list now.) What’s grotesque is a government hacking into the computers of millions of innocent people all over the world, without probable cause. It’s even worse if they are targeting people based on how radical their political views are. Of course it’s whistleblowing to expose violations of human rights, anywhere on Earth, no matter who does it, or whether they think it’s their job to do it.
Would it be alright if China hacked into the computers of people in the US who are, say, radically critical of China, in order to undermine their activities? Would it not be whistleblowing if someone exposed such a program?
I don’t know if they’re just going to ignore it or not but I just sent this story to all three of the local TV news channels and asked them how this story could possibly not be if interest to their viewers. I know it ain’t much but I just feel like I wanted to DO something.
Lets see if this post takes. First one has gone missing in action.
I would like to greet the new tracker here at the Intercept
Conviva.
I can’t live with them and the Intercept can’t live without them.
ConvivaPrivateLoader
https://www.ghostery.com/gcache/?n=Conviva&s=https%3A%2F%2Flivepassdl.conviva.com%2Fver%2F2.72.0.13589%2FLivePass.js&v=2&t=script
https://livepassdl.conviva.com/ver/2.72.0.13589/LivePass.js
After reading How the NSA Plans to Infect ‘Millions’ of Computers with Malware I searched my computer via regedit and found both TURBINE and HAMMERSTEIN in Microsoft Search Assist. deleted MSAssist
So the number of infected computers vastly exceeds the number of terrorists. This is yet another demonstration of the obvious: terrorism is an excuse, possibly even a reason, but the scope vastly exceeds anything anti-terrorism requires.
it is about power, of course, but what is not clear is this: why the specific programs described in this article? I would like to think that these programs are “required” because computer security is actually pretty damn good, and so they have to go to great lengths to subvert it. But I wonder if they actually simply do anything they can, even if they have other ways of obtaining the information. That is, explore and implement every possible way to steal information just because that is the ultimate path to power.
This is excusable hyperbole on your part. According to the NSA web site, there are currently a little over 7 billion terrorists and potential terrorists. The number of infected computers is nowhere near this high.
Thanks Common ‘Tater, I needed that. Very well played.
Now I know why Zelda thinks so highly of you and often quotes your little gems of wisdom.
Information is power, and company information, and corporate data including R&D, product information, planning and pricing is competitive advantage through industrial espionage. Its all legalized theft of information.
Guilty until proven innocent. Whenever something bad happens they will always have someone whose information somehow looks ‘suspicious’.
after reading How the NSA Plans to Infect “Millions” of Computers with Malware I searched my computer via regedit and found both TURBINE and HAMMERSTEIN in Microsoft Search Assistant. deleted all of search assistant.
That’s really frightening – if you documented it (I hesitate to say this) perhaps you could have had standing to sue the NSA.
I’m on a mac running mavericks OSX, any advice on how to search it for the same malware?
Intercept news stories like this never appear on the top of Google ‘News’ searches…
Go ahead, search “NSA Turbine” and all you’ll get is Gizmodo, BoingBoing, etc. stories covering it after The Intercept releases it.
Anyone else thing links to the intercept are being censored from the search results?
Glenn,
Snowden documents show how GD paranoid the people in the US Government are. They need to seek medical attention for their paranoia.
Do you think so?
They take paranoid-schizophrenic delusions to levels never seen before.
To tell you the truth, I am really afraid of those people. I am more afraid of them, than I am of any manufactured “Muslim Terrorist”.
Cope with that mate, totally
@Citizen… “manufactured” terror. Charming. After having near-epileptic seizures caused by rage (this morning) I took the day off from this to clear my head. You made me laugh – then I realized how right you are. Were is America? … at the mall?
“They need to seek medical attention for their paranoia.” … Are you kidding me? This morning I am GIDDY with the excitement of how this is think is shaking down. Someone pass me my maracas so I can fill them with their meds. That catchy tune they’ve been playin’? I’m in the percussion section and dancing my fat ass off to it! And the night is young…
I can’t abide these egostical a**holes like Snowden and Assange – they think they are “doing the right thing” when in fact it is the terrorists and other criminal fraternities that are the real winners from such leaks. Personally I don’t have a problem with what the NSA is doing – at the end of the day I’m a law abiding citizen.
Today this is what I had to deal with, trying to access the Intercept.
I fixed it for now but this shite happens all the time.
Pine Apple.
I obviously do not speak for Glenn … but … if it were me, I would not lay it all out at once because it would lead to overwhelming people to the point they would not properly absorb the gravity of the documents.
Facebook is going to love this.
Facebook is a wholly owned subsidiary
Where is that damn Like button when you need it?

It looks like a party or partner in crime and Whatsapp will extend the reach of surveillance.
You amswered in the “Ask Zelda” article? I’m sorry Glenn, but I cannot find your comments on this topic. Can you please be more specific – link?
Thanks.
Click on the article “Dispatches: The Intercept Welcomes Its New Editor and Two New Writers” and go to the update at the end of the article. If you need assistance, the NSA can provide the links. Don’t bother trying to contact Mr. Cook, as he is having trouble logging into Facebook this morning (he keeps getting a ‘packet redirect error’, but I’m looking into it for him).
I Think he means in the comments here: https://firstlook.org/theintercept/2014/03/10/intercept-welcomes-new-editor-two-new-writers/
What is up with these horrible slides that is coming from NSA? They all look like a 7-year olds work.
Like Yahoos UN presentation?I see the Zionists are still playing up that missile shipment.I think it was that NK freighter from a few months ago,reflagged by Panama,our erstwhile buddies.(Until we invade and arrest them,again).Man,evil never sleeps.
Regarding use of the term “hack” — do the NSA and CIA apply that term internally to the operations described in this article? Or do they eschew the term to maintain legal deniability? Recently we saw John Brennan emphatically say “we don’t hack.” Is that technically true by the rules of whatever lawyerish word game he is playing?
As internal documents indicate, they “own” computers, rather than “hack” them.
OuijaForestCat: Yes, the NSA does refer to the term “hack” internally. From one document cited in the article:
Yeah I saw that reference but it didn’t satisfy my curiosity. Does that one analyst’s embrace of the word “hack” reflect an agency-wide policy or is it just one guy’s opinion? And would the NSA/CIA use the word “hack” to describe all the practices listed in the article, or just some? And what if contractors or telecom employees are enlisted to perform the hacking? Would that maintain legal deniability?
There seems to be enough wiggle room for more “too cute by half” denials a la James Clapper.
typo: Computer Network Attack (CAN)
Dear Zelda,
I work in the cafeteria and I’m wondering if I should reduce the steroids in the stew. Some of the guys are acting quite aggressively. On the other hand, I know we need tough cyber warriors. Can you help?
Sincerely, Stewed ‘Tater
‘Tater,
Yes, by all means, cut back on the’roids.
As a supplement, you can increase the dosage of fluorides.
That outta keep ‘em in check for a while.
Docile Zelda.
Zelda,
Normally your advice is spot on. But if I do what you suggest, they may revert to becoming law abiding. What would happen to the TURBINE program?
Sincerely, Confused ‘Tater
We could convert the TURBINE program to a Whirl-li-gig and place it on the Capitol Dome. Al Gore could file for a tax rebate for reducing the Carbon Footprint of Government. They could sell the surplus power back into the grid……..
Glenn, what is your response to John Cook’s prior statements about your methods regarding NSA documents?
http://www.poynter.org/latest-news/top-stories/238702/foia-lessons-from-gawker-editor-john-cook/
“I love Glenn Greenwald,” Cook continued, “but he’s basically keeping the same secrets the NSA was
keeping” instead of “laying it all out there so people could look at it for themselves.”
I asked how Gawker would have handled Edward Snowden’s leaks, had he come to them instead of Greenwald, Laura Poitras and Barton Gellman.
“I would have read through everything,” he said. “I wouldn’t have put it up without reading it, but as quickly as practicable i would have put it all out there, and published every bit of it.”
I answered that when people asked about it … in the prior article that was actually about that.
Completely ignorant method. Glad he didn’t get the documents.
@Jason: “ignorant“ of what? Not protecting the people who committed these atrocities?? Because that’s what is done here. By keeping the names and locations and actual numbers a secret, they protect our enemies!
Ever heard of obstruction of justice?
Guess what: If you collaborate with criminals, you will be treated like criminals! If they worked at the NSA, then they are to be put in front of an international war court! And if you protect those NSA monsters, then for that reason you deserve the same.
Would you be willing to go to prison for doing the document dump? That’s what Greenwald would be facing if he dumped the files indiscriminately.
Brave of you to volunteer someone else to go to prison.
Right Liberalincalif, like we are glad Barefoot will, from his computer, spout off about how he would release names and wouldnt redact anything from the documents. Not very likely Barefoot! All your talk about collaborating with criminals is exactly what the NSA would brand someone who did this and the reckless release of the documents would likely convince others of that as well. Glenn did the right thing, he would have been doing the NSA a favor if he released the documents in full because it would be that much easier to paint him as a criminal and wanting to hurt agents out in the field and that is something others in power would most certainly sympathize with. He would have been picked apart by everyone and they’re mother like Wikileaks was.